P-2302R Series VoIP Station Gateway User's Guide
Table Of Contents
- P-2302R Series
- User’s Guide
- Copyright
- Federal Communications Commission (FCC) Interference Statement
- Safety Warnings
- ZyXEL Limited Warranty
- Customer Support
- Table of Contents
- List of Figures
- List of Tables
- Preface
- Introducing the Prestige
- Introducing the Web Configurator
- Wizard Setup
- System Screens
- LAN Setup
- WAN Screens
- Introduction to VoIP
- VoIP Screens
- Phone
- Phone Book
- Phone Usage
- Network Address Translation (NAT) Screens
- Static Route
- Firewall
- Content Filtering
- Remote Management Screens
- Universal Plug-and-Play (UPnP)
- Logs
- Bandwidth Management
- 19.1 Bandwidth Management Overview
- 19.2 Bandwidth Classes and Filters
- 19.3 Proportional Bandwidth Allocation
- 19.4 Application-based Bandwidth Management
- 19.5 Subnet-based Bandwidth Management
- 19.6 Application and Subnet-based Bandwidth Management
- 19.7 Scheduler
- 19.8 Maximize Bandwidth Usage
- 19.9 Bandwidth Borrowing
- 19.10 Configuring Summary
- 19.11 Configuring Class Setup
- 19.12 Configuring Monitor
- Maintenance
- Introducing the SMT
- General Setup
- WAN Setup
- LAN Setup
- Internet Access
- Remote Node Configuration
- Static Route Setup
- Network Address Translation (NAT)
- Enabling the Firewall
- Filter Configuration
- SNMP Configuration
- System Information and Diagnosis
- Firmware and Configuration File Maintenance
- 33.1 Filename Conventions
- 33.2 Backup Configuration
- 33.2.1 Backup Configuration
- 33.2.2 Using the FTP Command from the Command Line
- 33.2.3 Example of FTP Commands from the Command Line
- 33.2.4 GUI-based FTP Clients
- 33.2.5 TFTP and FTP over WAN Management Limitations
- 33.2.6 Backup Configuration Using TFTP
- 33.2.7 TFTP Command Example
- 33.2.8 GUI-based TFTP Clients
- 33.3 Restore Configuration
- 33.4 Uploading Firmware and Configuration Files
- System Maintenance
- Remote Management
- Call Scheduling
- Troubleshooting
- 37.1 Problems Starting Up the Prestige
- 37.2 Problems with the LAN Interface
- 37.3 Problems with the WAN Interface
- 37.4 Problems with Internet Access
- 37.5 Problems with the Password
- 37.6 Problems with the Web Configurator
- 37.7 Problems with a Telephone or the Telephone Port
- 37.8 Problems with Voice Service
- 37.9 Pop-up Windows, JavaScripts and Java Permissions
- Product Specifications
- Wall-mounting Instructions
- Setting up Your Computer’s IP Address
- IP Subnetting
- PPPoE
- Triangle Route
- SIP Passthrough
- Index
P-2302R Series User’s Guide
Chapter 18 Logs 190
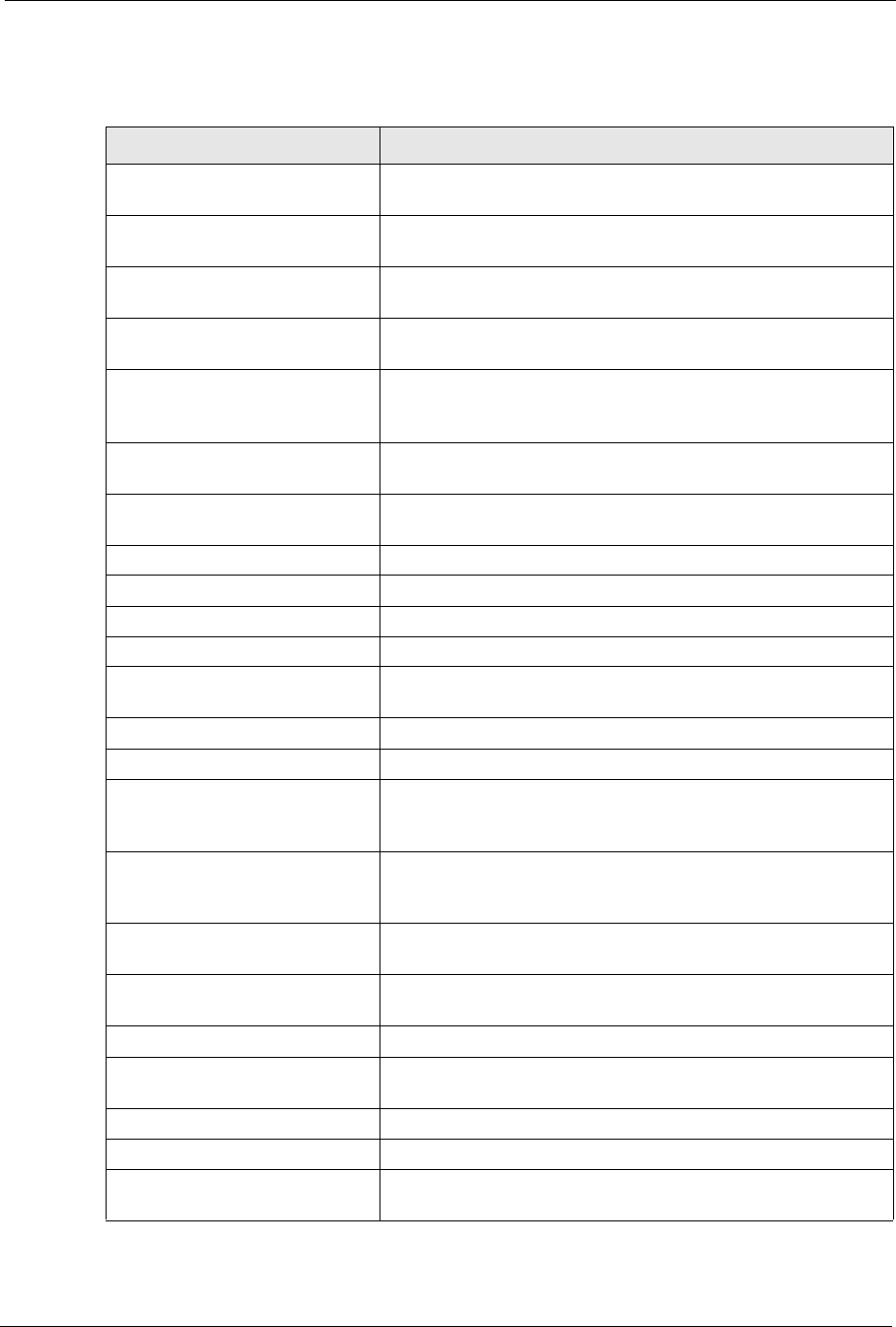
For type and code details, see Table 67 on page 191.
Table 65 Attack Logs
LOG MESSAGE DESCRIPTION
attack [ TCP | UDP | IGMP
| ESP | GRE | OSPF ]
The firewall detected a TCP/UDP/IGMP/ESP/GRE/OSPF attack.
attack ICMP (type:%d,
code:%d)
The firewall detected an ICMP attack.
land [ TCP | UDP | IGMP |
ESP | GRE | OSPF ]
The firewall detected a TCP/UDP/IGMP/ESP/GRE/OSPF land
attack.
land ICMP (type:%d,
code:%d)
The firewall detected an ICMP land attack.
ip spoofing - WAN [ TCP |
UDP | IGMP | ESP | GRE |
OSPF ]
The firewall detected an IP spoofing attack on the WAN port.
ip spoofing - WAN ICMP
(type:%d, code:%d)
The firewall detected an ICMP IP spoofing attack on the WAN port.
icmp echo : ICMP
(type:%d, code:%d)
The firewall detected an ICMP echo attack.
syn flood TCP The firewall detected a TCP syn flood attack.
ports scan TCP The firewall detected a TCP port scan attack.
teardrop TCP The firewall detected a TCP teardrop attack.
teardrop UDP The firewall detected an UDP teardrop attack.
teardrop ICMP (type:%d,
code:%d)
The firewall detected an ICMP teardrop attack.
illegal command TCP The firewall detected a TCP illegal command attack.
NetBIOS TCP The firewall detected a TCP NetBIOS attack.
ip spoofing - no routing
entry [ TCP | UDP | IGMP |
ESP | GRE | OSPF ]
The firewall classified a packet with no source routing entry as an
IP spoofing attack.
ip spoofing - no routing
entry ICMP (type:%d,
code:%d)
The firewall classified an ICMP packet with no source routing entry
as an IP spoofing attack.
vulnerability ICMP
(type:%d, code:%d)
The firewall detected an ICMP vulnerability attack.
traceroute ICMP (type:%d,
code:%d)
The firewall detected an ICMP traceroute attack.
ports scan UDP The firewall detected a UDP port scan attack.
Firewall sent TCP packet in
response to DoS attack TCP
The firewall sent TCP packet in response to a DoS attack
ICMP Source Quench ICMP The firewall detected an ICMP Source Quench attack.
ICMP Time Exceed ICMP The firewall detected an ICMP Time Exceed attack.
ICMP Destination Unreachable
ICMP
The firewall detected an ICMP Destination Unreachable attack.










