manual
Table Of Contents
- Contents
- Overview
- Situation – Description
- Solution
- Technical Concept
- Conclusion
- Appendix A – Delta Airlines Access Examples
- Appendix B Local Network Logon
- Appendix C – The VASCO VRM & Tokens work with BM
- About VASCO Data Security
(Fig 1b) Once this is done, the application owner will assign those Digipass secrets to their
end-users. This assignment is done based on the serial number of the Digipass token and the
name of the end-user. The Digipass token is then shipped to the end-user together with a
manual and the protected PIN-code on a secure PIN-mailer.
Once the token is received by the end-user, he can start using it. To use a Digipass you need a
connection to the host (server) computer that knows the secrets of the end-user’s Digipass
token. Every time the user sends a dynamic password or digital signature to the host
computer, the computer will get all the necessary information from the database and will
check the validity of the password or signature. After the host has checked the validity of the
dynamic password or signature, he will notify the end-user of the correctness or incorrectness
of the validity check
Configuration Parameters
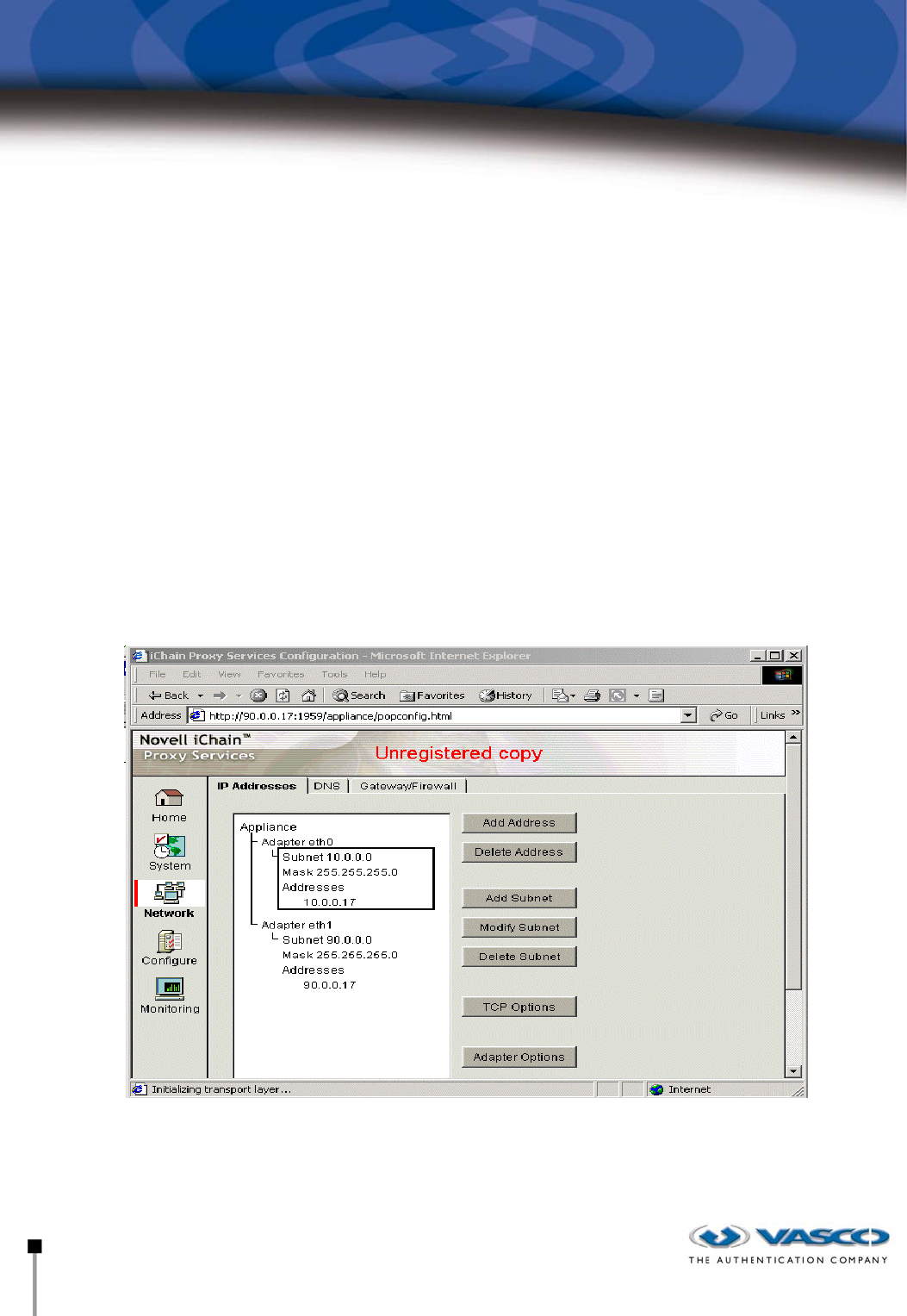
Configuration of IChain
Fig 2. Configuration of IP address for proxying
As access is needed from an external resource to an internal resource, two subnets are
configured in order to handle all requests from outside. As in our example with the Delta
www.vasco.com ∙ Using Digipass Strong User Authentication with Novell NMAS and ICHAIN ∙ 9










