User's Manual
© 2010 - 2015 Persistent Systems, LLC – All Rights Reserved 33
STEP 1: LOAD CONFIGURATION FILE INTO ALL OTHER NODES
When setting up a network of new nodes from the factory, use the configuration
file saved in the “Store Configuration File” step to upload the settings from the
previously configured node into the new node. During this process, node specific
settings (including IP Address, Radio Name, and other radio specific settings) can
be configured separately for each node while preserving all other settings from the
configuration file.
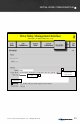
1. Click “Node Configuration” > “Config Management.”
2. In the Load Configuration menu, select “network (require all)” or “network (any
available)” to upload configuration settings to all nodes in the network. The
“network (require all)” setting will require all nodes in the network be available
for any changes to be applied. If not all nodes are available, no changes will be
applied. The “network (any available)” setting will apply changes to available
nodes only.
3. Click the “Choose File” button to find the the configuration file saved in the
“Store Configuration File” step.
4. Click the “Load” button to upload configuration settings to other nodes in the
network.
STEP 2: LOAD KEY INTO ALL OTHER NODES
The security key is NOT stored in the configuration file. You must load the key
separately.
1. Select the “Security” tab in the Web Management Interface.
2. In the “Set Key” box, select “network (require all)” or “network (any available)”
to upload the security key to all nodes in the network. The “network (require
all)” setting will require all nodes in the network be available for any changes
to be applied. If not all nodes are available, no changes will be applied. The
“network (any available)” setting will apply changes to available nodes only.
3. Select the Crypto Mode chosen in Step 6 of First Node Configuration from the
drop-down menu.
4. Copy the security key from the text file saved in Step 6 of First Node Configura-
tion and paste the security into the “Enter key” field. All nodes MUST have the
same security key to communicate.
INITIAL NODE CONFIGURATION