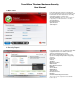
Trend Micro Titanium Maximum Security User Manual 1. Main Panel In the main panel by a large icon and the bar has been protective level of your computer, and below it there are three main areas of security and status indicator on your license. Security Summary: when use this menu there is appearing new window which is showing Security Report Parental Controls: System Tuner: Subscription: 2.
3. System tuner System Tuner service can help you recover disk space, can make the launch of Microsoft ® Windows ® more quickly to clear your stories of instant messaging programs and to optimize the performance of your computer. You can even adjust automatically improve the performance of your computer and make his work more smooth and seamless. More of that data link: What is System Tuner? 4. Parental Control Parental Control gives you ability to determine how people use the Internet from this computer.
5. Tools Form Tools button in main screen you can access: Parental Controls System Tuner Secure Erase Data Thief Prevention Trend Micro Vault Free Tool Center 6.
7. Parental Control Getting Started The first time you try to use the Parental Controls, you will be asked if you have set any separate Microsoft Windows User Accounts on the computer. By setting up separate accounts for your kids, you can configure different rules for them by linking each Windows User Accounts to the Parental Controls. Otherwise, the same rules will apply to everyone using the computer.
9. Parental Control - settings Age Group Categories Blocked Ages 3-7 (Child) Ages 8-12 (Pre-teen) Ages 13-17 (Teen) All categories are blocked by default for young children.
11. Parental Control - settings System Tuner optimizes your computer's performance and helps protect your privacy on the Internet. Before making any changes, System Tuner also backs up your system settings. 12. Parental Control - settings What benefits does System Tuner provide? System Tuner can offer the following enhancements to your computer: Disk space — System Tuner checks for recoverable disk space in temporary folders, the Recycle Bin, and other locations.
button menu. Instant messaging privacy — To help maintain your privacy online, System Tuner can remove chat histories, recent screen names, lists of files downloaded, transaction logs, and other information generated by using Windows Live (MSN) Messenger, AOL Instant Messenger (AIM), and Yahoo! Messenger. 13. Secure Erase When you delete a file, Microsoft Windows just removes the directory information used to find it.
15. Data Theft Prevention - settings This tool can protect sensitive personal information, such as credit card numbers or passwords for online services. Upon detecting any attempt to send protected information to the Internet, whether to a web page, by email or through an instant message, the transmission can be blocked automatically.
18. Main Panel - scanning You can choose from three types of scans:: Quick Scan Scans only the places where threats commonly hide Full Scan Scans the entire computer, including any external drives, except network drives Custom Scan Scans everything in the folders that you select 19. Protection settings Keep your computer protected Your security software analyzes basic information about every file that you open, save, or download.
Mark the Conduct a scheduled scan of the computer checkbox to check your files and settings for hidden threats. Use the lists under the checkbox to select when the scan should begin. Choose a time when you would normally not use the computer very much after switching it on, like lunchtime on a Friday. Maximize your protection Your security software can not only search for threats in files and settings, but also check for suspicious behavior on your computer.
20. Protection settings Trend Micro maintains a database of risky websites that have a history of transmitting malicious software or supporting online fraud. Follow the directions below to protect yourself from unsafe sites. Mark the Block potentially dangerous websites checkbox to protect against threats on the Internet automatically. Choose one of the three levels of protection against Web threats: High Prevents you from opening sites that pose even a slight risk of transmitting viruses and spyware.
21. Protection settings To help keep yourself safe on the Internet at home or on the go, you should mark both of these checkboxes. Mark the Activate the Firewall Booster to enhance the protection given by the Windows Firewall checkbox to configure the Windows Firewall so that it can offer better protection against online threats.
23. Protection settings If you use email software on your computer, then you can use this feature to intercept unwanted email messages. Mark the Filter out unsolicited advertisements and other unwanted email messages checkbox to activate the Trend Micro Anti-Spam toolbar in supported versions of Microsoft® Outlook®, Microsoft® Outlook® Express, and Windows Mail. 24.
25. Protection settings Click the Add button to open a window for selecting a file or folder to put on the list. You can only add one file or folder at a time. You can only use the Remove button after marking the checkbox next to at least one thing on the list. 26. Protection settings Websites You can use this exception list to specify websites that should either always or never be blocked from opening.
27. Protection settings Click the Add button to open a window for selecting a website to put on the list. After typing an address, select whether to block or trust that website from the dropdown list next to Response. You can click the Remove button after marking the checkbox next to at least one thing on the list. 28. Protection settings Wireless connection Any wireless network identified as risky or dangerous that you have decided to trust will appear on this exception list.
29. Protection settings Your security software can load drivers and services gradually to help your computer start up as quickly as possible, or load them all immediately to provide the strongest security as soon as possible. Select Extra Security if you care most about protecting the computer as much as possible as soon as possible. You might have to wait a little bit longer for Microsoft Windows to launch when the computer starts.
31. Protection settings The Trend Micro Smart Protection Network™ automatically correlates information about security risks found on millions of computers worldwide to help develop protection against new threats more quickly. The more people participate, the more effective this network becomes. Note: No personal information is gathered or shared. Mark the Share threat information with Trend Micro checkbox to help Trend Micro better protects you. 32.
33.