User Guide
Table Of Contents
- Package Contents
- Chapter 1 About this Guide
- Chapter 2 Introduction
- Chapter 3 Login to the Switch
- Chapter 4 System
- Chapter 5 Switching
- Chapter 6 VLAN
- Chapter 7 Spanning Tree
- Chapter 8 Multicast
- Chapter 9 QoS
- Chapter 10 ACL
- Chapter 11 Network Security
- Chapter 12 SNMP
- Chapter 13 LLDP
- Chapter 14 Cluster
- Chapter 15 Maintenance
- Chapter 16 System Maintenance via FTP
- Appendix A: Specifications
- Appendix B: Configuring the PCs
- Appendix C: 802.1X Client Software
- Appendix D: Glossary
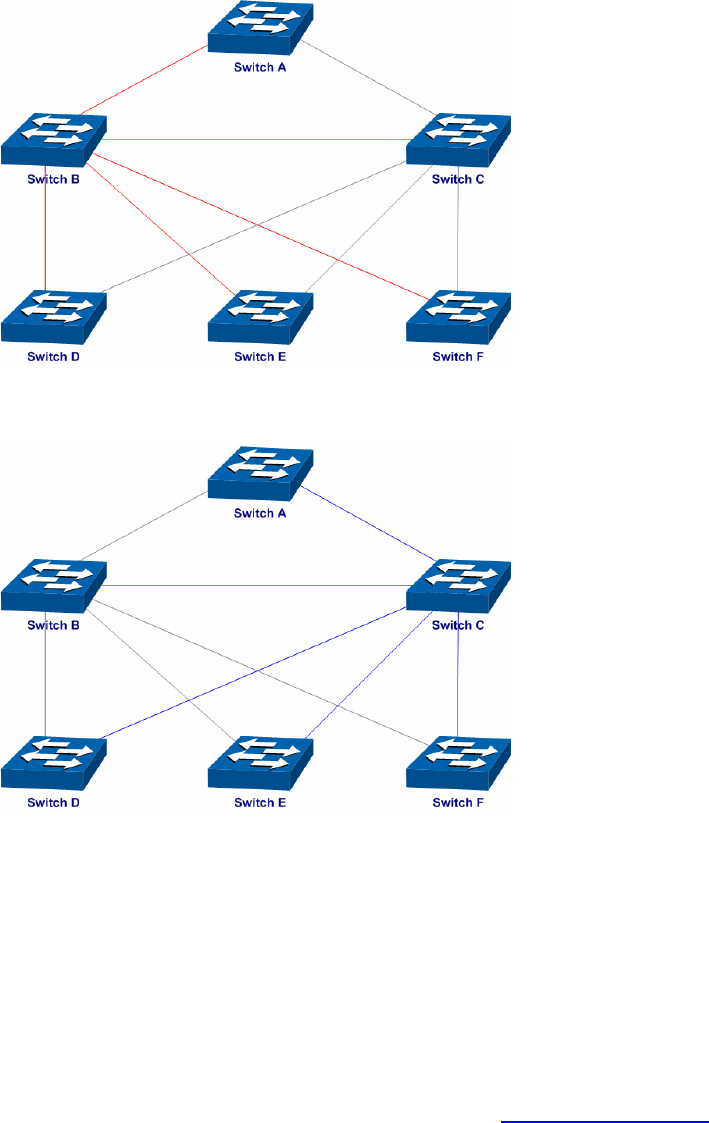
The configuration procedure for switch E and F is the same with that for switch D.
The topology diagram of the two instances after the topology is stable
For Instance 1 (VLAN 101, 103 and 105), the red paths in the following figure are connected
links; the gray paths are the blocked links.
For Instance 2 (VLAN 102, 104 and 106), the blue paths in the following figure are connected
links; the gray paths are the blocked links.
Suggestion for Configuration
Enable TC Protect function for all the ports of switches.
Enable Root Protect function for all the ports of root bridges.
Enable Loop Protect function for the non-edge ports.
Enable BPDU Protect function or BPDU Filter function for the edge ports which are connected to
the PC and server.
Return to CONTENTS
97










