User Manual Part 3
Table Of Contents
- Introduction
- 1.1 New Features
- 1.2 Feature Overview
- 1.2.1 Single or Dual Mode Radio Options
- 1.2.2 Separate LAN and WAN Ports
- 1.2.3 Multiple Mounting Options
- 1.2.4 Antenna Support for 2.4 GHz and 5.2 GHz Radios
- 1.2.5 Sixteen Configurable WLANs
- 1.2.6 Support for 4 BSSIDs per Radio
- 1.2.7 Quality of Service (QoS) Support
- 1.2.8 Industry Leading Data Security
- 1.2.9 VLAN Support
- 1.2.10 Multiple Management Accessibility Options
- 1.2.11 Updatable Firmware
- 1.2.12 Programmable SNMP v1/v2/v3 Trap Support
- 1.2.13 Power-over-Ethernet Support
- 1.2.14 MU-MU Transmission Disallow
- 1.2.15 Voice Prioritization
- 1.2.16 Support for CAM and PSP MUs
- 1.2.17 Statistical Displays
- 1.2.18 Transmit Power Control
- 1.2.19 Advanced Event Logging Capability
- 1.2.20 Configuration File Import/Export Functionality
- 1.2.21 Default Configuration Restoration
- 1.2.22 DHCP Support
- 1.2.23 Multi-Function LEDs
- 1.3 Theory of Operations
- Hardware Installation
- Getting Started
- System Configuration
- Network Management
- Configuring Access Point Security
- 6.1 Configuring Security Options
- 6.2 Setting Passwords
- 6.3 Enabling Authentication and Encryption Schemes
- 6.4 Configuring Kerberos Authentication
- 6.5 Configuring 802.1x EAP Authentication
- 6.6 Configuring WEP Encryption
- 6.7 Configuring KeyGuard Encryption
- 6.8 Configuring WPA Using TKIP
- 6.9 Configuring WPA2-CCMP (802.11i)
- 6.10 Configuring Firewall Settings
- 6.11 Configuring VPN Tunnels
- 6.12 Configuring Content Filtering Settings
- 6.13 Configuring Rogue AP Detection
- 6.14 Configuring User Authentication
- Monitoring Statistics
- Command Line Interface Reference
- Configuring Mesh Networking
- Technical Specifications
- Usage Scenarios
- Customer Support
- Index
Usage Scenarios
B-11
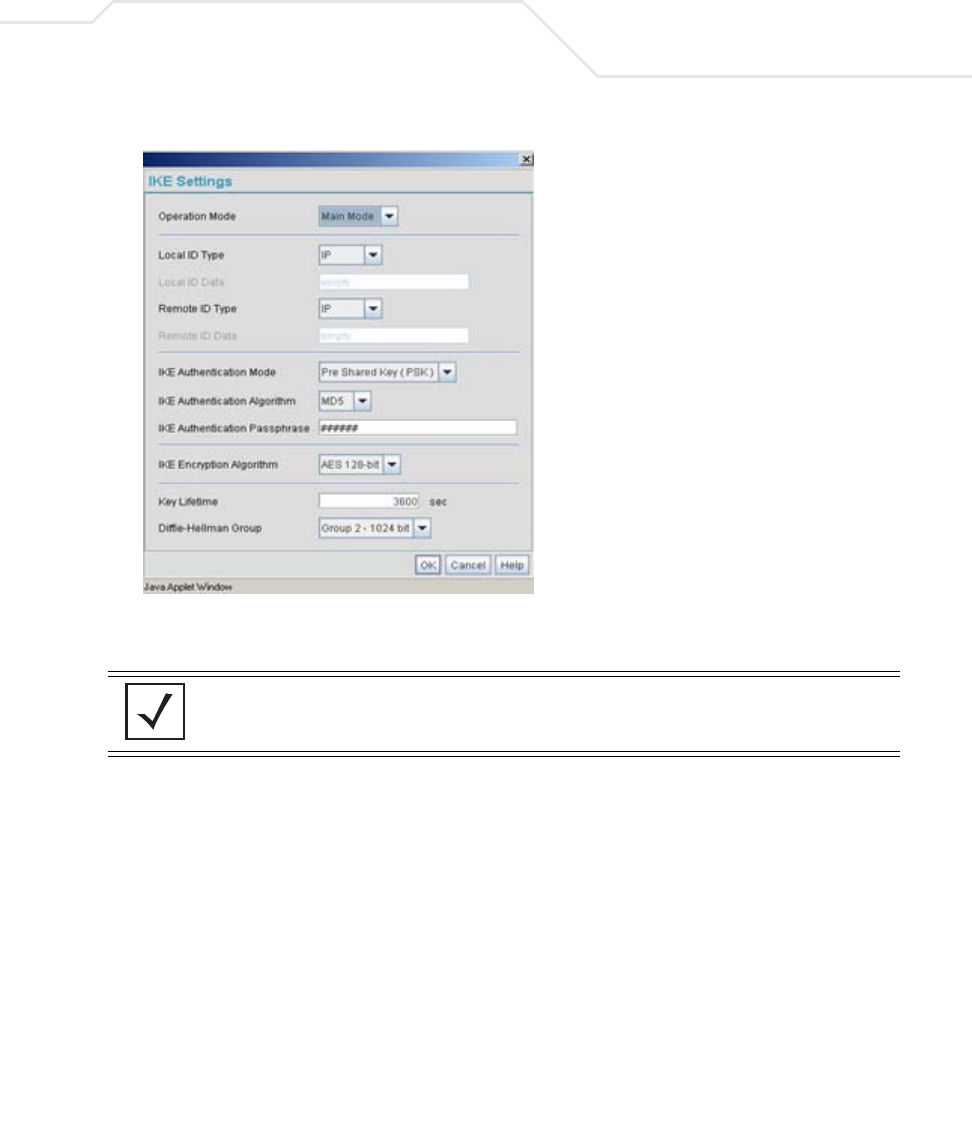
13. Select Pre Shared Key (PSK) from the IKE Authentication Mode drop-down menu.
14. Enter a Passphrase. Passphrases must match on both VPN devices.
15. Select AES 128-bit as the IKE Encryption Algorithm.
16. Select Group 2 as the Diffie -Hellman Group. Click OK. This will take you back to the VPN
screen.
17. Click Apply to make the changes
18. Check the VPN Status screen. Notice the status displays "NOT_ACTIVE". This screen
automatically refreshes to get the current status of the VPN tunnel. Once the tunnel is
active, the IKE_STATE changes from NOT_CONNECTED to SA_MATURE.
NOTE Ensure the IKE authentication Passphrase is the same as the Pre-shared
key on the Cisco PIX device.










