User Manual
Table Of Contents
- Document Contents
- SonicWALL NSA E6500
- Pre-Configuration Tasks
- Registering Your Appliance
- Deployment Scenarios
- Selecting a Deployment Scenario
- Scenario A: NAT/Route Mode Gateway
- Scenario B: State Sync Pair in NAT/Route Mode
- For network installations with two SonicWALL NSA E-Series appliances configured as a stateful synchronized pair for redundant high-availability networking.
- In this scenario, one SonicWALL NSA E6500 operates as the primary gateway device and the other SonicWALL NSA E6500 is in passive...
- Scenario C: L2 Bridge Mode
- In this scenario, the original gateway is maintained. The SonicWALL NSA E6500 is integrated seamlessly into the existing network...
- Initial Setup
- System Requirements
- Connecting the WAN Port
- Connecting the LAN Port
- Applying Power
- Accessing the Management Interface
- Accessing the Setup Wizard
- Connecting to Your Network
- Testing Your Connection
- Activating Licenses in SonicOS
- Upgrading Firmware on Your SonicWALL
- Obtaining the Latest Firmware
- Saving a Backup Copy of Your Preferences
- Upgrading the Firmware
- Using SafeMode to Upgrade Firmware
- Configuring a State Sync Pair in NAT/Route Mode
- Configuring L2 Bridge Mode
- Selecting a Deployment Scenario
- Additional Deployment Configuration
- Support and Training Options
- Rack Mounting Instructions
- Product Safety and Regulatory Information
Page 44 Creating Network Access Rules
• Select the from and to zones from the From Zone and
To Zone menus.
• Select the service or group of services affected by the
access rule from the Service list. If the service is not
listed, you must define the service in the Add Service
window. Select Create New Service or Create New
Group to display the Add Service window or Add
Service Group window.
• Select the source of the traffic affected by the access
rule from the Source list. Selecting Create New
Network displays the Add Address Object window.
• Select the destination of the traffic affected by the
access rule from the Destination list. Selecting
Create New Network displays the Add Address
Object window.
• From the Users Allowed menu, add the user or user
group affected by the access rule.
• Select a schedule from the Schedule menu. The
default schedule is Always on.
• Enter any comments to help identify the access rule in
the Comments field.
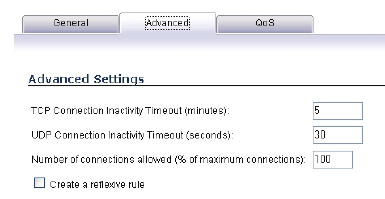
4. Click on the Advanced tab.
• If you would like for the access rule to timeout after a
different period of TCP inactivity, set the amount of
time, in minutes, in the TCP Connection Inactivity
Timeout (minutes) field. The default value is 60
minutes.
• If you would like for the access rule to timeout after a
different period of UDP inactivity, set the amount of
time, in minutes, in the UDP Connection Inactivity
Timeout (minutes) field. The default value is 30
minutes.
• Specify the number of connections allowed as a
percent of maximum number of connections allowed
by the SonicWALL security appliance in the Number
of connections allowed (% of maximum
connections) field.
• Select Create a reflexive rule if you want to create a
matching access rule to this one in the opposite
direction--from your destination zone or address
object to your source zone or address object.
NSA_E6500_GSG.book Page 44 Wednesday, June 17, 2009 7:16 PM










