User Manual
Intended Operation Environment (Including Deployment Options)
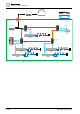
Isolated Network Deployment
3
20 | 28
A6V11917735_en_b_41
Zone Boundary Protection
● The Cerberus DMS isolated network is a security zone physically protected (for
example, locked in a rack in the server room). It uses separated networks that
only permit restricted access to its components.
● An exception can be made for a temporary connection open for maintenance
remote access to be closed immediately after the operation has been
completed.
● A separate VLAN alone does not meet the requirements for Zone Boundary
Protection. A firewall is also required.
● In case one of the allowed components is remote, a physically protected and
secured communication is also required through
tunneling
that enables the
users to create a virtual network between two remote points on an existing
public IP network and communicate through a VPN.
● The Zone Boundary Protection must be implemented through VPN and firewall
to limit the inbound and outbound communication to temporary exception for
maintenance remote access.
3.2 Isolated Network Deployment
Isolated Local Network
An isolated local network consists of servers that are connected in an environment
which has no connection to any other network. In this model, there is zero network
connectivity to a larger internal network or the Internet. Since there is no potential
for remote exploits from a large number of unknown sources, this environment
provides well defined physical, network, and security characteristics.
By definition, the access to this configuration is limited to personnel with access to
the trusted admin hosts on the closed local network. Threats consist of an
accidental connection being made to other networks, a trusted admin installing an
unsigned package, or an application that might inject a malware agent.
Guidelines for the isolated local network model:
● Set all default passwords for uniqueness and complexity.
● Limit physical access to essential personnel.
● Avoid installing untrusted third-party software.