User Manual
Network Security Controls
Protected System Configuration Concept
2
28 | 88
A6V11646120_enUS_c_41
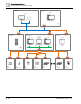
Figure 2: Zone Boundary Protection
Customer IT
Local Office
DCC Client
DCC WSI
Customer IT
DMZ
HTML5
Tomcat
IIS
Firewall
BIRT
MySQL
Customer IT
Server Backbone
DCC
Server Backbone
DCC
Control Room
DCC Client
HTML5
DCC Server
DCC Client /
DCC WSI /
DCC Server
DCC FEP
WinCC OA WinCC OA
WinCC OA
Tomcat
IIS
BIRT
MySQL
DCC
Desigo PX
DCC
Desigo SiPass
DCC
FS20
DCC
System One
DCC
SPC
DCC
Subsystem n
DCC
Subsystem m
Cameras Cameras VMSSystem One
FS20
SiPass
Desigo PX