User`s guide
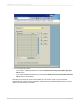
The "Authorization field values" screen appears.
10.
In the Field value list, type the equals sign (=) and the name of the field that you want to secure.
For this example, you would type =BUKRS.
Tip:
To view a list of available fields, right-click the Field value list and, on the shortcut menu, click Possible
entries. Double-click the desired field (in this case, BUKRS) to insert it along with the required equals
sign (=).
11.
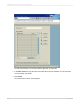
Click Save.
12.
Exit the Security Definition Editor.
13.
Following your usual procedure, apply the new authorization object to the profiles or roles of the
appropriate users.
For instance, following this example, you would apply the Z_BUKRS authorization object to each
user who needs to access rows of data within the GLT0 table. When you apply the authorization
object, you enter the appropriate Company Code values into the BUKRS authorization field, thereby
specifying the Company Codes that the specified user is authorized to access.
Depending on the version of R/3 or mySAP ERP that you are using, and the SAP authorization
model that you have already deployed, you can accomplish this in various ways:
• Attach the new authorization to a new role that you in turn add to each user's security profile.
• Attach the new authorization to a new profile that you in turn add to each user's security profile.
The end result is that the authorization is added to the master user data, so the database drivers
can adhere to your customized data access restrictions.
Securing rows using custom security exits
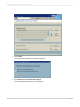
In addition to, or instead of using authorization-based restrictions for tables, you can secure rows using
custom security exits. That is, you can map table fields to function parameters so that you can define
the call to one function to handle the post filtering for any table.
Note:
• You must give a value (either constant or field-mapped) for all non-optional parameters.
• Make mappings between compatible types. For example, do not link a function parameter for a date
to a number field. Mapping incompatible types results in a failure at runtime.
The following example shows how to map table fields to function parameters in a custom security exit.
To define row-level security using a custom security exit
1.
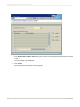
Execute transaction /CRYSTAL/RLS.
2.
In the Table name field, type the name of the data table whose rows you want to secure.
For this example, type PA0000 to secure the rows in that table.
2012-03-14620
Integrating Business Applications with Crystal Reports