Installation guide
Finally, you must decide whether to enable SSL using the checkbox at the bottom. Red Hat
strongly recommends that you employ this level of encryption for all traffic to and from the RHN
Proxy Server. T o select it, however, you must connect to the central RHN Servers (which have SSL
enabled by default) or to an RHN Satellite Server or RHN Proxy Server that has SSL enabled.
Connection to the central RHN Servers requires upload of the certificate tar file mentioned earlier.
Connection to a Satellite or another Proxy through SSL requires the CA certificate password used
in enabling SSL on the parent system.
Note
Refer to the chapter entitled "SSL Infrastructure" in the Red Hat Network Client
Configuration Guide for more information about configuring a secure RHN Proxy Server
infrastructure using SSL.
If you choose not to enable SSL during installation, leave this box unchecked and refer to the SSL
Certificates chapter of the RHN Client Configuration Guide to learn how to obtain this level of
security post install. When finished, click continue. If you enabled SSL and are connecting to a
Satellite, the Configure SSL page appears. If you enabled SSL and are connecting to another
Proxy or the central RHN servers, the Upload SSL page appears. If you did not enable SSL but
did enable Monitoring, skip to the description of the Configure Monitoring page. If you did
not enable SSL or Monitoring, skip to the description of the Install Progress page.
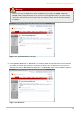
Figure A.6. Configure SSL
14. In the Configure SSL page applicable only to a Proxy connecting to an RHN Satellite Server
with SSL enabled, provide the information needed to generate the server certificate. T he most
important item is the CA certificate password, which must match the password used while
enabling SSL on the parent server. The remaining fields may match the parent server's values but
can differ depending on the role of the RHN Proxy Server, for instance reflecting a different
geographic location. Similarly, the email address may be the same one provided earlier for the
Proxy administrator, but may instead be directed to a particular certificate administrator. Certificate
expiration is configurable. As always, ensure that the values provided here exist in the backups of
information described in Chapter 2, Requirements. Once finished, click continue.
Red Hat Network Satellite 5.3 Proxy Installation Guide
32