User guide
More Secure Use
2-89
More Secure Use
Communication data and authentication information between servers are encrypted in the Interstage
Single Sign-on system. The following two methods make operation more secure:
Using Ipsec
IPsec is the encryption communication protocol defined as the standard protocol of the Virtual Private
Network (VPN) by IETF. IPsec encrypts data on the IP protocol level. Therefore, higher-level protocols
and applications need not be changed for the encryption.
Since communication between servers is protected on the IP protocol level by using IPsec, more secure
operation can be made to prevent electrical interception or alteration.
To use IPsec, set up IPsec so that IPsec encryption communication is performed between all of the
Interstage-Single-Sign-on repository servers, authentication servers, and business servers. IPsec is
provided as the standard function of the operating system from Windows ® 2000 or Solaris 8 0E.
Using firewall
A firewall controls access to data that flows between networks.
Using a firewall, authentication servers and repository servers can be set in an independent, secure
network. Since accesses using the Interstage Single Sign-on system are controlled, invalid accesses
are avoided.
To use a firewall, separately prepare a firewall product.
Using IPsec
To use IPsec, set up IPsec on all of the Interstage-Single-Sign-on repository servers, authentication
servers, and business servers so that IPsec encryption communication can be performed between
these servers.
IPsec provides encryption of communication data in the following cases:
• Communication between business server and repository server
• Communication between authentication server and repository server
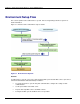
The following shows an example of Interstage Single Sign-on configuration using IPsec in which
authentication-server load distribution and repository-sever availability are considered.