Installation guide
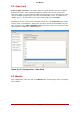
Figure 29.9. Authentication
In the Authentication section, select whether to use shadow passwords and MD5 encryption
for user passwords. These options are highly recommended and chosen by default.
The Authentication Configuration options allow you to configure the following methods of au-
thentication:
• NIS
• LDAP
• Kerberos 5
• Hesiod
• SMB
• Name Switch Cache
These methods are not enabled by default. To enable one or more of these methods, click the
appropriate tab, click the checkbox next to Enable, and enter the appropriate information for the
authentication method. Refer to the Red Hat Enterprise Linux Deployment Guide for more in-
formation about the options.
7. Firewall Configuration
The Firewall Configuration window is similar to the screen in the installation program and the
Security Level Configuration Tool.
7. Firewall Configuration
287