Installation guide
4. Enter a Met h o d N ame for the fencing method that you are configuring for this node. This is
an arbitrary name that will be used by Red Hat High Availability Add-On; it is not the same as
the DNS name for the device.
5. Click Submi t. This displays the node-specific screen that now displays the method you have
just added under Fen ce D evices.
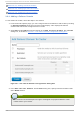
6. Configure a fence instance for this method by clicking the Add Fence Instance button that
appears beneath the fence method. This displays the Ad d Fen ce Device ( In st an ce) drop-
down menu from which you can select a fence device you have previously configured, as
described in Section 3.6.1, “Creating a Fence Device” .
7. Select a fence device for this method. If this fence device requires that you configure node-
specific parameters, the display shows the parameters to configure. For information on
fencing parameters, refer to Appendix A, Fence Device Parameters.
Note
For non-power fence methods (that is, SAN/storage fencing), Un f en cin g is selected
by default on the node-specific parameters display. This ensures that a fenced node's
access to storage is not re-enabled until the node has been rebooted. When you
configure a device that requires unfencing, the cluster must first be stopped and the full
configuration including devices and unfencing must be added before the cluster is
started. For information on unfencing a node, refer to the fence_no d e(8) man page.
8. Click Submi t. This returns you to the node-specific screen with the fence method and fence
instance displayed.
3.7.2. Configuring a Backup Fence Device
You can define multiple fencing methods for a node. If fencing fails using the first method, the system
will attempt to fence the node using the second method, followed by any additional methods you
have configured.
Use the following procedure to configure a backup fence device for a node.
1. Use the procedure provided in Section 3.7.1, “Configuring a Single Fence Device for a Node”
to configure the primary fencing method for a node.
2. Beneath the display of the primary method you defined, click Ad d Fence Metho d .
3. Enter a name for the backup fencing method that you are configuring for this node and click
Submi t. This displays the node-specific screen that now displays the method you have just
added, below the primary fence method.
4. Configure a fence instance for this method by clicking Ad d Fence Instance. This displays
a drop-down menu from which you can select a fence device you have previously configured,
as described in Section 3.6.1, “ Creating a Fence Device”.
5. Select a fence device for this method. If this fence device requires that you configure node-
specific parameters, the display shows the parameters to configure. For information on
fencing parameters, refer to Appendix A, Fence Device Parameters.
6. Click Submi t. This returns you to the node-specific screen with the fence method and fence
instance displayed.
Red Hat Ent erprise Linux 6 Clust er Administ rat ion
50