Installation guide
Note
Fence devices that are in use cannot be deleted. To delete a fence device that a node is
currently using, first update the node fence configuration for any node using the device and
then delete the device.
To delete a fence device, follow these steps:
1. From the Fen ce Devices configuration page, check the box to the left of the fence device or
devices to select the devices to delete.
2. Click D el ete and wait for the configuration to be updated. A message appears indicating
which devices are being deleted.
When the configuration has been updated, the deleted fence device no longer appears in the display.
3.7. Configuring Fencing for Clust er Members
Once you have completed the initial steps of creating a cluster and creating fence devices, you need
to configure fencing for the cluster nodes by following the steps in this section. Note that you must
configure fencing for each node in the cluster.
The following sections provide procedures for configuring a single fence device for a node,
configuring a node with a backup fence device, and configuring a node with redundant power
supplies:
Section 3.7.1, “ Configuring a Single Fence Device for a Node”
Section 3.7.2, “ Configuring a Backup Fence Device”
Section 3.7.3, “ Configuring a Node with Redundant Power”
3.7.1. Configuring a Single Fence Device for a Node
Use the following procedure to configure a node with a single fence device.
1. From the cluster-specific page, you can configure fencing for the nodes in the cluster by
clicking on No d es along the top of the cluster display. This displays the nodes that
constitute the cluster. This is also the default page that appears when you click on the cluster
name beneath Man ag e Clu st ers from the menu on the left side of the lu ci Ho meb ase
page.
2. Click on a node name. Clicking a link for a node causes a page to be displayed for that link
showing how that node is configured.
The node-specific page displays any services that are currently running on the node, as well
as any failover domains of which this node is a member. You can modify an existing failover
domain by clicking on its name. For information on configuring failover domains, see
Section 3.8, “ Configuring a Failover Domain” .
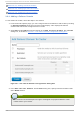
3. On the node-specific page, under Fen ce Devices, click Ad d Fence Metho d . This displays
the Ad d Fence Metho d to No d e dialog box.
Chapt er 3. Configuring Red Hat Hig h Availabilit y Add- O n Wit h Conga
4 9