Installation guide
Co n f ig u rat io n page. After selecting the daemon, you can check whether to log the debugging
messages for that particular daemon. You can also specify the sysl o g and log file settings for that
daemon.
Click Apply for the logging configuration changes you have specified to take effect.
3.6. Configuring Fence Devices
Configuring fence devices consists of creating, updating, and deleting fence devices for the cluster.
You must configure the fence devices in a cluster before you can configure fencing for the nodes in
the cluster.
Creating a fence device consists of selecting a fence device type and entering parameters for that
fence device (for example, name, IP address, login, and password). Updating a fence device consists
of selecting an existing fence device and changing parameters for that fence device. Deleting a fence
device consists of selecting an existing fence device and deleting it.
Note
It is recommended that you configure multiple fencing mechanisms for each node. A fencing
device can fail due to network split, a power outage, or a problem in the fencing device itself.
Configuring multiple fencing mechanisms can reduce the likelihood that the failure of a
fencing device will have fatal results.
This section provides procedures for the following tasks:
Creating fence devices — Refer to Section 3.6.1, “ Creating a Fence Device” . Once you have
created and named a fence device, you can configure the fence devices for each node in the
cluster, as described in Section 3.7, “Configuring Fencing for Cluster Members”.
Updating fence devices — Refer to Section 3.6.2, “ Modifying a Fence Device” .
Deleting fence devices — Refer to Section 3.6.3, “ Deleting a Fence Device” .
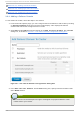
From the cluster-specific page, you can configure fence devices for that cluster by clicking on Fen ce
Devices along the top of the cluster display. This displays the fence devices for the cluster and
displays the menu items for fence device configuration: Ad d and Delet e. This is the starting point of
each procedure described in the following sections.
Note
If this is an initial cluster configuration, no fence devices have been created, and therefore
none are displayed.
Figure 3.5, “ luci fence devices configuration page” shows the fence devices configuration screen
before any fence devices have been created.
Chapt er 3. Configuring Red Hat Hig h Availabilit y Add- O n Wit h Conga
4 7