Specifications
Copyright © 2015. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of Tenable Network Security, Inc.
21
Installation
Downloading Nessus
Download the latest version of Nessus from the Nessus download page or through the Tenable Support Portal. Confirm
the integrity of the installation package by comparing the download MD5 checksum with the one listed in the product
release notes. Nessus 6 is available for Windows 7, Server 2008, Server 2008 R2, Server 2012, Server 2012 R2, and
Windows 8.
Nessus distribution file sizes and names vary slightly from release to release, but are approximately 25 MB in size.
Installing
Nessus is distributed as an executable installation file. Place the file on the system it is being installed on or a shared
drive accessible by the system.
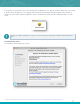
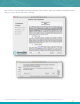
Download the file Nessus-6.x.x-x64.msi, and then double-click on it. This will start the install procedure.
You must install Nessus using an administrative account and not as a non-privileged user. If you receive any errors
related to permissions, “Access Denied”, or errors suggesting an action occurred due to lack of privileges, ensure that you
are using an account with administrative privileges. If you receive these errors while using command line utilities, run
cmd.exe with “Run as…” privileges set to “administrator”.
Some antivirus software packages can classify Nessus as a worm or some form of malware. This is due to the
large number of TCP connections generated during a scan. If your AV software gives a warning, click on
“allow” to let Nessus continue scanning. Most AV packages allow you to add processes to an exception list as
well. Add Nessus.exe and Nessus-service.exe to this list to avoid such warnings.
It is recommended that you obtain a plugin feed activation code before starting the installation process, as that information
will be required before you can authenticate to the Nessus GUI interface. For more information on obtaining an activation
code, read the section titled Vulnerability Plugins.