Gigabit Ethernet Switch User's Manual
Table Of Contents
- Chapter 1. Introduction
- Chapter 2. Installing the Switch
- Chapter 3. Switch Management
- Chapter 4. Console Interface
- 4.1 Login Screen
- 4.2 Main Menu
- 4.3 System Information Menu
- 4.4 Management Setup Menu
- 4.5 Device Control Menu
- 4.5.1 Setting the System Operation Mode
- 4.5.2 Layer 2 Menu
- 4.5.3 Using the Bridge Menu
- 4.5.4 Configuring Virtual LANs
- 4.5.5 Configuring IGMP Snooping
- 4.5.6 Configuring IP Settings
- 4.5.7 Security Menu
- 4.5.8 Jumbo Packet Configuration
- 4.6 Monitoring the Switch
- 4.6.1 Displaying Port Statistics
- 4.6.2 Layer 2 Address Tables
- 4.6.3 Displaying Bridge Information
- 4.6.4 Displaying VLAN Information
- 4.6.5 IP Multicast Registration Table
- 4.6.6 IP Address Table
- 4.7 Resetting the System
- 4.8 Logging Off the System
- Chapter 5. Web Interface
- 5.1 Web-Based Configuration and Monitoring
- 5.2 Navigating the Web Browser Interface
- 5.3 Panel Display
- 5.4 Main Menu
- 5.5 System Information Menu
- 5.6 Management Setup Menu
- 5.7 Device Control Menu
- 5.7.1 Layer 2 Menu
- 5.7.2 Using the Bridge Menu
- 5.7.3 Configuring Virtual LANs
- 5.7.4 Configuring IGMP Snooping
- 5.7.5 Configuring IP Settings
- 5.7.6 Configuring Security Filters
- 5.7.7 Jumbo Packet Configuration
- 5.8 Monitoring the Switch
- 5.9 Resetting the System
- Chapter 6.Advanced Topics
- Appendix A Troubleshooting
- Appendix B Pin Assignments
- GLOSSARY
WGS3 Layer 3 Switch User’s Manual
- 199 -
5.7.6 Configuring Security Filters
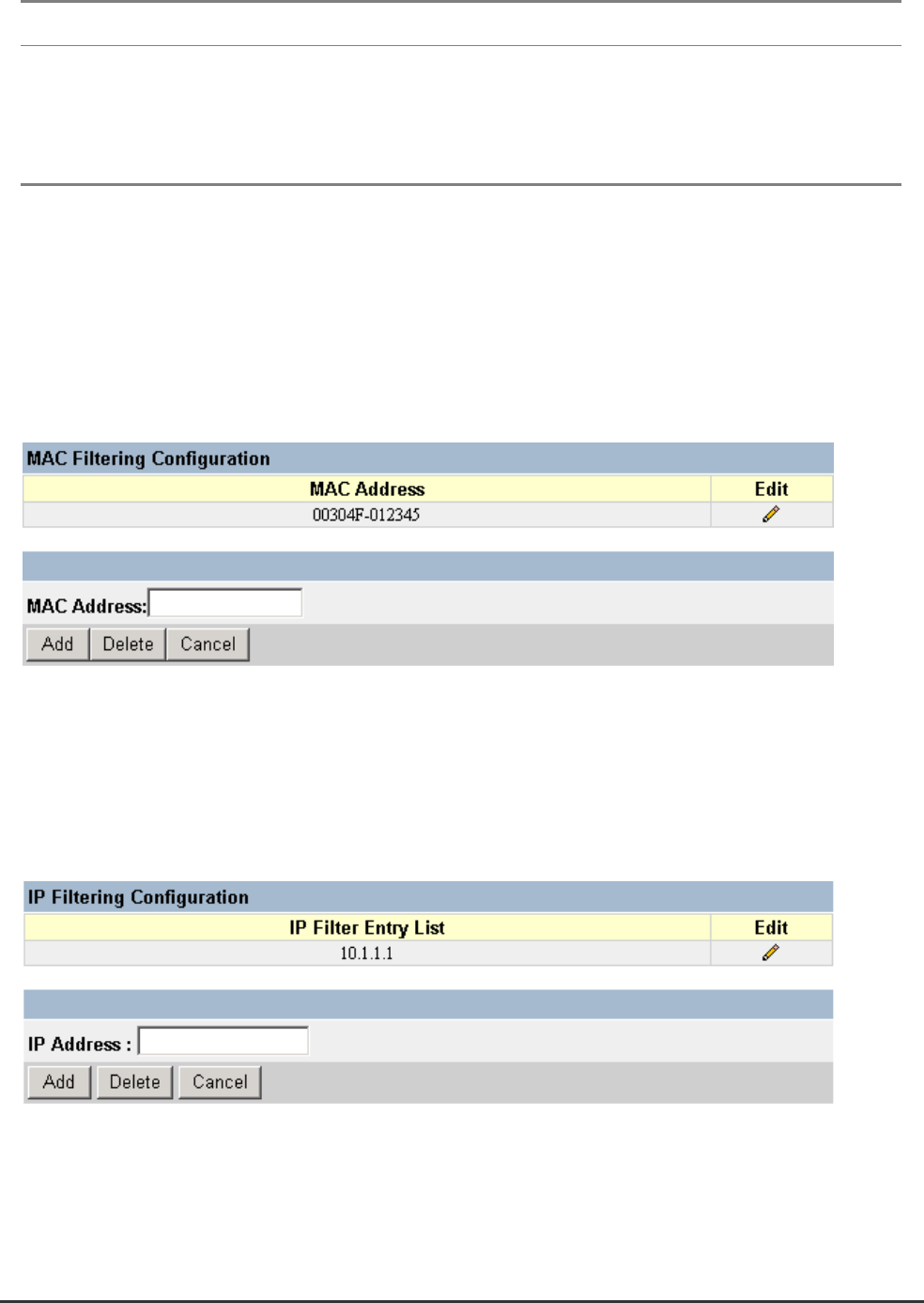
You can use the Security menu to filter MAC and IP addresses.
Parameter Description
MAC Filtering
Configuration
Specifies the source or destination MAC address for any traffic to be filtered from the
switch.
IP Filtering
Configuration*
Specifies the source or destination IP address for any traffic to be filtered from the
switch.
* This menu item is only displayed for WGS3-404 or multilayer mode of WGS3-2620.
5.7.6.1 Configuring MAC Address Filters
Any node that presents a security risk or is functioning improperly can be filtered from this switch. You
can drop all the traffic from a host device based on a specified MAC address. Traffic with either a source
or destination address listed in the Security Filtering Configuration table will be filtered.
5.7.6.2 Configuring IP Address Filters
If any node presents a security risk, you can filter all traffic for this node by entering its address into the
IP Security Filter. Any packet passing through the switch that has a source or destination IP address
matching an entry in this table will be filtered.










