Operation Manual
Plug-Ins
45
exploited by well known Trojan horses. Click the tab according to the list you want to
change.
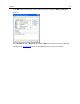
Click Add and specify the Protocol, Port number and Weight. Weight is a decimal value
that indicates port importance. A greater number indicates a more vulnerable port. You
may also add comments to describe the port’s purpose or anything you wish to note.
There can be computers on your network that you are absolutely sure are not a source of
danger for your system, as well as ports on your system you are sure cannot serve as an
intruder’s backdoor. In other words, you consider that monitoring these hosts and/or ports
is fruitless and wish to conserve your system’s resources and increase its performance by
not monitoring them.
The Outpost Firewall Attack Detection plug-in features exclusion lists to which you can
add hosts and ports you don't want to have monitored. To manage these lists, click Hosts or
Ports under Exclusions in the Advanced tab of the plug-in settings dialog.