SpeedTouchTM608WL and SpeedTouchTM620 only SpeedTouchTM608(WL)/620
Table Of Contents
- Contents
- About this IPSec Configuration Guide
- 1 IPSec: Concept for secure IP connections
- 2 SpeedTouch™ IPSec terminology
- 3 Configuration via Local Pages
- Prerequisites
- IPSec Web Pages
- VPN Menu
- In this section
- 3.1 LAN to LAN Application
- Reference network
- Selecting the LAN to LAN application
- Outline of a configuration procedure
- 3.1.1 Remote Gateway Address Known Page
- VPN context
- Initial page
- Buttons
- Remote Gateway
- Miscellaneous
- IKE Security Descriptors
- Page layout with additional Descriptors
- Page layout for pre- shared key authentication
- IKE Authentication with Preshared Key
- Page layout for certificate authentication
- IKE Authentication: Certificate parameters
- Example of a completed page
- Buttons
- 3.1.2 Remote Gateway Address Unknown Page
- VPN context
- Example
- Aggressive Mode initial page
- Aggressive Mode versus Main Mode
- Buttons
- Miscellaneous
- IKE Security Descriptors
- Page layout with additional Descriptors
- Page layout for pre- shared key authentication
- IKE Authentication with Preshared Key
- Page layout for certificate authentication
- IKE Authentication: Certificate parameters
- Main Mode initial page
- Buttons
- IKE Security Descriptors
- Page layout with additional Descriptors
- Miscellaneous
- Page layout for pre- shared key authentication
- IKE Authentication with Preshared Key
- Page layout for certificate authentication
- IKE Authentication: Certificate parameters
- Main mode expanded page
- Identification & Interface
- Example of a completed page
- Buttons
- 3.1.3 Connections Page
- 3.2 VPN Client
- VPN context
- Advantages of the SpeedTouch™ VPN Client
- Selecting the VPN Client application
- Outline of a VPN Client configuration procedure
- 3.2.1 VPN Client Page
- Initial page
- Buttons
- Server IP Address or FQDN
- Backup Server IP Address or FQDN
- IKE Security Descriptor
- IPSec Security Descriptor
- Exchange Mode
- Server Vendor
- Primary Untrusted Physical Interface
- Virtual IP mapping
- Optional Remote network
- Page layout for pre- shared key authentication
- IKE Authentication with Preshared Key
- Page layout for certificate authentication
- IKE Authentication: Certificate parameters
- Starting and stopping a VPN client connection
- Page layout for Automatic Start
- Local LAN IP Range
- Set of Server Vendor specific parameters
- Configuring XAuth
- 3.2.2 Starting the VPN Client Connection
- 3.2.3 Closing a Connection
- 3.3 VPN Server
- VPN context
- Selecting the VPN Server application
- Outline of a VPN server configuration procedure
- 3.3.1 VPN Server Page
- Initial page
- Buttons
- Local Trusted Network
- Page layout with additional Networks
- IKE Security Descriptor
- Page layout with additional Descriptors
- IPSec Security Descriptor
- Page layout with additional Descriptors
- Miscellaneous
- VPN Server settings
- Page layout for pre- shared key authentication
- IKE Authentication with Preshared Key
- Page layout for certificate authentication
- IKE Authentication: Certificate parameters
- Authorized Users List
- 3.4 Certificates
- 3.5 Advanced VPN Menu
- When to use
- Peer Profiles page
- Connection Profiles page
- 3.5.1 Peer Profiles Page
- 3.5.2 Authentication Page
- 3.5.3 Peer Descriptors Page
- 3.5.4 Peer Options Page
- 3.5.5 VPN-Client Page
- 3.5.6 VPN-Server Page
- 3.5.7 VPN-Server-XAuth Page
- 3.5.8 Connection Profiles Page
- 3.5.9 Networks Page
- 3.5.10 Connection Descriptors Page
- 3.5.11 Connection Options Page
- 3.5.12 Client Page
- 4 Configuration via the Command Line Interface
- In this chapter
- Reference network
- 4.1 Basic IPSec configuration procedure
- 4.2 Peer: Authentication Attribute
- 4.3 Peer Security Descriptor
- 4.4 Peer
- What is ...
- How is it used
- In this section
- 4.4.1 Peer parameters
- Parameters table
- Peer name [name]
- Remote Security Gateway identifier [remoteaddr]
- Backup remote Security Gateway Identifier [backupaddr]
- Exchange mode [exchmode]
- Local Identifier [localid]
- Remote Identifier [remoteid]
- Physical Interface [phyif]
- Peer descriptor [descr]
- Authentication Attribute [auth]
- client/server
- options
- 4.4.2 List all peer entities
- 4.4.3 Create a new peer entity
- 4.4.4 Set or modify the peer parameters
- 4.4.5 Delete a Peer entity
- 4.5 Connection Security Descriptor
- 4.6 Network Descriptor
- 4.7 Connection
- 4.8 Auxiliary Commands
- 4.9 Organisation of the IPSec Command Group
- 5 Troubleshooting SpeedTouch™ IPSec
- 6 Advanced Features
- In this section
- 6.1 IPSec and the Stateful Inspection Firewall
- 6.2 Surfing through the VPN tunnel
- 6.3 Extended Authentication (XAuth)
- 6.4 VPN Client
- 6.5 VPN Server
- 6.6 XAuth Users Pool
- Introduction
- 6.6.1 XAuth Pool parameters
- 6.6.2 Create a new XAuth pool
- 6.6.3 Modify the xauthpool type
- 6.6.4 Attach the xauthpool entity to the vpnserver entity
- 6.6.5 Delete an xauthpool entity
- 6.6.6 XAuth User parameters
- 6.6.7 Create a new XAuth user
- 6.6.8 Set or modify the password of an XAuth user
- 6.6.9 Delete an xauthuser entity
- 6.7 The Default Peer Concept
- 6.8 One Peer - Multiple Connections
- 6.9 Peer Options
- 6.10 Connection Options
- 6.11 Advanced Connection
- Need more help?
Chapter 1
IPSec: Concept for secure IP connections
E-DOC-CTC-20051017-0169 v1.0
13
Internet Key Exchange The Internet Key Exchange (IKE) protocol is the negotiation protocol used to establish
an SA by negotiating security protocols and exchanging keys. First the IKE SA is set
up, then the IKE channel acts as a signalling channel to negotiate a general purpose
SA.
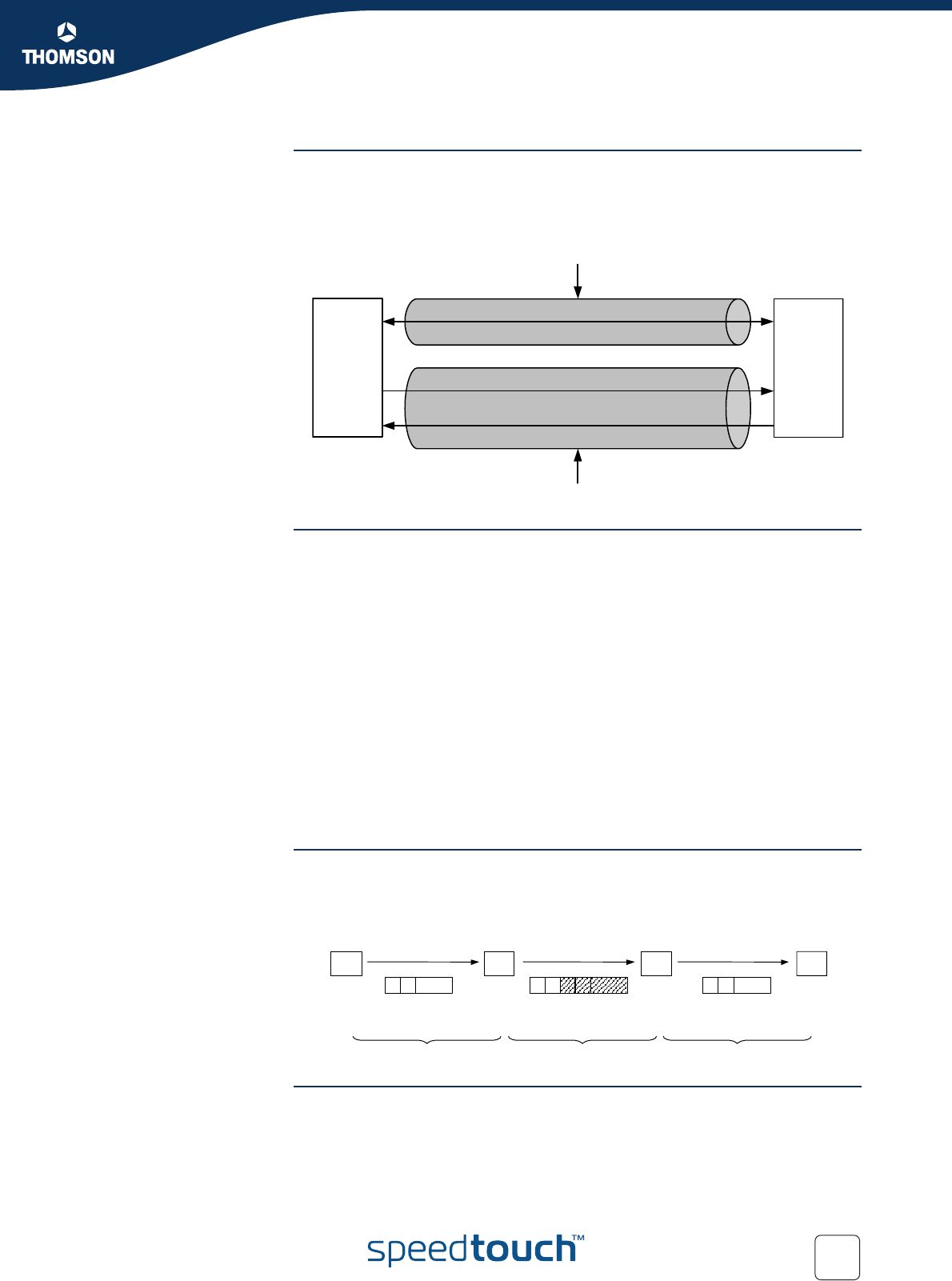
Security Associations Within the IKE protocol, two phases are distinguished to set up a tunnel between
two peers:
Phase 1: negotiate a bi-directional IKE SA functioning as a signalling channel to
negotiate the Phase 2 SAs.
Phase 2: negotiate unidirectional IPSec Security Associations that will carry
general purpose traffic.
The IKE SA is bidirectional, whereas the Phase 2 SA is unidirectional: one Security
Association must be set up in each direction. The initiator and responder cookies
uniquely identify an IKE SA while each PH2 SA is uniquely identified by a SPI
(Security Parameter Index) value.
Per convention, throughout this document the IKE SA is referred to as the Phase 1
SA and the ESP SAs are referred to as the Phase 2 SA:
Phase 1 SA = IKE SA = secure Phase 1 tunnel
A pair of Phase 2 SAs = a secure Phase 2 tunnel
Tunnel Mode Using tunnel mode, the complete IP packet (including its IP header) is encapsulated
and a new IP header is attached. This allows for the original source and destination IP
addresses to be hidden from the outside world.
Transport Mode In transport mode, the IP header is transported unmodified. The use of transport
mode is limited to connections where the security gateway is acting as a host, e.g.,
for network management applications. When the SpeedTouch™ is managed from a
remote location via a VPN connection, transport mode can be used, because in this
case the SpeedTouch™ is the end user of this information stream.
Phase 1
Phase 2 tunnel
Phase 1 (IKE) SA
SA (ESP/AH)
SA (ESP/AH)
CDAB
AB C D
AB AB
Red network
node
Red network
node
SpeedTouch620 [1] SpeedTouch620 [2]
Red LAN Black LAN Red LAN










