Quick Reference Guide
Table Of Contents
- Reference Manual for the Model DG834 ADSL Firewall Router
- Contents
- Chapter 1 About This Guide
- Chapter 2 Introduction
- Chapter 3 Connecting the Router to the Internet
- What You Need Before You Begin
- Connecting the DG834 to Your LAN
- Auto-Detecting Your Internet Connection Type
- Testing Your Internet Connection
- Manually Configuring Your Internet Connection
- Chapter 4 Protecting Your Network
- Chapter 5 Managing Your Network
- Chapter 6 Advanced Configuration
- Chapter 7 Troubleshooting
- Appendix A Technical Specifications
- Appendix B Network and Routing Basics
- Appendix C Preparing Your Network
- Preparing Your Computers for TCP/IP Networking
- Configuring Windows 95, 98, and Me for TCP/IP Networking
- Configuring Windows NT4, 2000 or XP for IP Networking
- DHCP Configuration of TCP/IP in Windows XP, 2000, or NT4
- Configuring the Macintosh for TCP/IP Networking
- Verifying the Readiness of Your Internet Account
- Restarting the Network
- Glossary
Reference Manual for the Model DG834 ADSL Firewall Router
4-8 Protecting Your Network
• WAN Users
These settings determine which packets are covered by the rule, based on their source
(WAN) IP address. Select the desired option:
• Any — all IP addresses are covered by this rule.
• Address range — if this option is selected, you must enter the Start and Finish fields.
• Single address — enter the required address in the Start fields.
•Log
You can select whether the traffic will be logged. The choices are:
• Never — no log entries will be made for this service.
• Always — any traffic for this service type will be logged.
• Match — traffic of this type which matches the parameters and action will be logged.
• Not match — traffic of this type which does not match the parameters and action will
be logged.
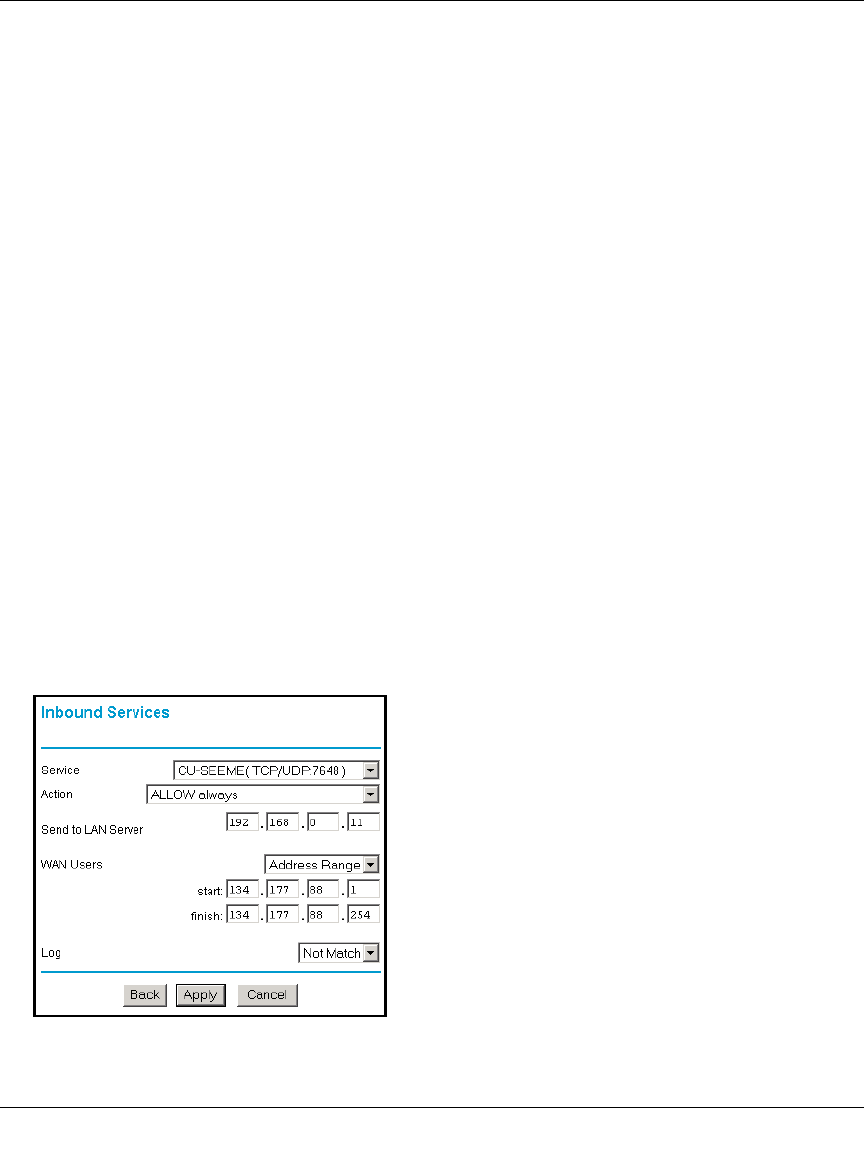
Inbound Rule Example: Allowing Videoconferencing
If you want to allow incoming videoconferencing to be initiated from a restricted range of outside
IP addresses, such as from a branch office, you can create an inbound rule. In the example shown
in Figure 4-6, CU-SeeMe connections are allowed only from a specified range of external IP
addresses. In this case, we have also specified logging of any incoming CU-SeeMe requests that
do not match the allowed parameters.
Figure 4-6: Rule example: Videoconference from Restricted Addresses










