User's Manual
www
S
S
Sec
u
bet
w
SSH
S
S
To
c
.netcommwireless.com
S
H Ke
y
u
re Shell (SSH) is U
N
w
een machines. It w
a
uses RSA public ke
y
Use
a
Use
a
S
H Server
C
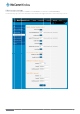
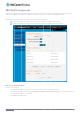
onfigure the SSH se
r
1.
Use the SS
2.
Select the
t
authentica
t
3.
Click the S
a
y
Mana
g
N
IX-based command
a
s designed as a rep
y
cryptography for b
o
a
utomatically genera
t
a
manually generate
d
C
onfigur
a
r
ver settings:
H Protocol drop do
w
t
ypes of authenticati
o
t
ion methods on but
y
a
ve button to confir
m
g
eme
n
interface and netwo
lacement for Telnet
a
o
th connection and
a
t
ed public-private ke
y
d
public-private key
p
a
tion
w
n list to select the p
r
o
n you want to use b
y
y
ou may not turn the
m
m
your settings.
n
t
r
k protocol used to g
a
nd other insecure r
e
a
uthentication. Two
c
y
pairs to encrypt th
e
p
air to perform the a
u
Figure
1
r
otocol that you want
y
clicking the Enable
m
both off.
g
ain secure access t
o
e
mote shell protocols
c
ommon ways of usi
n
e
network connectio
n
u
thentication and all
o
1
0
1
- SSH Server Co
nf
to use. Protocol 2 is
e
password authentic
o
a remote compute
r
which send informa
t
n
g SSH are:
n
and then use pass
w
o
w users or program
s
f
iguratio
n
more recent and is
c
ation and Enable ke
y
N
e
,
execute command
s
t
ion, including pass
w
w
ord authentication t
o
s
to log in without usi
n
c
onsidered more sec
y
authentication togg
etComm Wireless 3G
s
on a remote machi
n
w
ords, as plain text.
o
log on.
ng a password.
c
ure.
g
le keys on or off. No
t
Light Industrial M2M
R
n
e or to transfer files
t
e that you may have
R
oute
r
107
both