Specifications
Configuring HotSpot 8-5
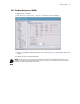
primary RADIUS server. To authenticate a hotspot user with a RADIUS server through a VPN tunnel select
the bind interface from the Bind Intf (for Pri Server) drop down.
If the RADIUS server is on a network accessible through a VPN tunnel, then the tunnel must be
configured. The bind interface should be the same as the Local Subnet configured for the VPN tunnel.
Entering information for the secondary RADIUS server is optional.
To authenticate a hotspot user with a RADIUS server, select the authentication mode from the Radius
auth-mode drop down. You can use either PAP or CHAP as the authentication mode.
To use the RADIUS server located on the WS2000, click the Use Local Radius button. This sets the
value of the Primary RADIUS Server IP to 127.0.0.1, the port to 1812. Enter the common secret for access
in the Pri Secret field. You can also provide information for an external secondary RADIUS server.
Radius Accounting Logs
4. The Radius Accounting area provides a feature by which user logins and logouts can be logged. This user
accounting information can be sent to an external RADIUS server or to the installed CF card. using the
onboard RADIUS server.
To enable logging of RADIUS accounting to the CF card, select the Enable Accounting (Save to CF
Card) option.
Enter the Timeout value which is the duration (in seconds) for retransmitting the accounting request to
the RADIUS server if no response is received from the server. The timeout value should be between 1-
255 sec.
Enter the Retries value which is the number of times the accounting request is sent to the RADIUS server
if no response is received, before logging is done on to the CF Card. The value should be between 1-10.
White List Entries
5. The White List is a list of URLs the hotspot users can access without authentication. A maximum of 10
URLs can be created for each WLAN.
Click White List Entries button to enter and manage White List entries for the WLAN.