User's Manual
SettingȱupȱtheȱServerȱConsoleȱ
SpectraGuard
®
ȱEnterpriseȱInstallationȱGuideȱ
73
ȱ
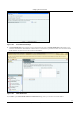
Figure 100. Intrusion Prevention Policy
Youȱcanȱenableȱintrusionȱpreventionȱagainstȱtheȱfollowingȱthreats:ȱ
x RogueȱAPs:ȱAPsȱthatȱareȱconnectedȱtoȱyourȱnetworkȱbutȱnotȱauthorizedȱbyȱtheȱadministrator;ȱanȱattackerȱcanȱgainȱ
accessȱtoȱyourȱnetworkȱthroughȱtheȱRogueȱAPs.ȱYouȱcanȱalsoȱautomaticallyȱquarantineȱUncategorizedȱIndeterminateȱ
andȱBannedȱAPsȱconnectedȱtoȱtheȱnetwork.
ȱ
x MisȬconfiguredȱAPs:ȱAPsȱthatȱareȱauthorizedȱbyȱtheȱadministratorȱbutȱdoȱnotȱconformȱtoȱtheȱsecurityȱpolicy;ȱanȱ
attackerȱcanȱgainȱaccessȱtoȱyourȱnetworkȱthroughȱmisconfiguredȱAPs.ȱThisȱcouldȱhappenȱifȱtheȱAPsȱareȱreset,ȱ
tamperedȱwith,ȱorȱifȱthereȱisȱaȱchangeȱinȱtheȱsecurityȱpolicy.ȱ
x Client
ȱMisȬassociation:ȱAuthorizedȱClientsȱthatȱconnectȱtoȱRogueȱorȱExternalȱ(neighboring)ȱAPs;ȱcorporateȱdataȱonȱ
theȱAuthorizedȱClientȱisȱunderȱthreatȱdueȱtoȱsuchȱconnections.ȱAirTightȱrecommendsȱthatȱyouȱprovideȱautomaticȱ
intrusionȱpreventionȱagainstȱAuthorizedȱClientsȱthatȱconnectȱtoȱExternalȱAPs.ȱ
x UnauthorizedȱAssociations:ȱUnauthorizedȱandȱBannedȱClientsȱthatȱconnectȱto
ȱAuthorizedȱAPs;ȱanȱattackerȱcanȱgainȱ
accessȱtoȱyourȱnetworkȱthroughȱAuthorizedȱAPsȱifȱtheȱsecurityȱmechanismsȱareȱweak.ȱUnauthorizedȱorȱ
UncategorizedȱClientȱconnectionsȱtoȱanȱAuthorizedȱAPȱusingȱaȱGuestȱSSIDȱareȱnotȱtreatedȱasȱunauthorizedȱ
associations.ȱ
x AdȱhocȱConnections:ȱPeerȬtoȬpeerȱconnectionsȱbetweenȱClients;ȱ
corporateȱdataȱon
ȱtheȱAuthorizedȱClientȱisȱunderȱ
threatȱifȱitȱisȱinvolvedȱinȱanȱadȱhocȱconnection.ȱ
x MACȱSpoofing:ȱAnȱAPȱthatȱspoofsȱtheȱwirelessȱMACȱaddressȱofȱanȱAuthorizedȱAP;ȱanȱattackerȱcanȱlaunchȱanȱattackȱ
throughȱaȱMACȱspoofingȱAP.ȱ
x Honeypot/EvilȱTwinȱAPs:ȱNeighboringȱAPsȱthatȱhaveȱtheȱsameȱ
SSIDȱasȱanȱAuthorizedȱAP;ȱAuthorizedȱClientsȱcanȱ
connectȱtoȱHoneypot/EvilȱTwinȱAPs.ȱCorporateȱdataȱonȱtheseȱAuthorizedȱClientsȱisȱunderȱthreatȱdueȱtoȱsuchȱ
connections.ȱ
x DenialȱofȱServiceȱ(DoS)ȱAttacks:ȱDoSȱattacksȱdegradeȱtheȱperformanceȱofȱanȱofficialȱWLAN.ȱ
x WEPGuardȱ
TM
:ȱActiveȱWEPȱcrackingȱtoolsȱallowȱattackersȱtoȱcrackȱtheȱWEPȱkeyȱandȱgainȱaccessȱtoȱconfidentialȱdataȱ
inȱaȱmatterȱofȱminutesȱorȱevenȱseconds.ȱCompromisedȱWEPȱkeysȱareȱusedȱtoȱgainȱentryȱintoȱtheȱauthorizedȱWLANȱ
byȱspoofingȱtheȱMACȱaddressȱofȱanȱinactiveȱAuthorizedȱClient.ȱ