Specifications
9
To determine approximately how many events you should have on your network use the following
formula:
(10,000 nodes) x (1 to 2 million events) = estimated number of events
For example, if you have 50,000 nodes you should be in the range of 5 to 10 million total client and
threat events.
This number will vary greatly based on the number of products and
policies you have and your data retention rate. Do not panic if you
exceed this number.
If you significantly exceed this number determine why you have so many events. Sometimes this
can be normal if you receive a significant number of viruses. This is common in unrestricted
networks like universities or college campuses. Another reason for a high event count could be how
long you keep the events in your database before purging. Here is what to check:
• Are you purging your events on a regular basis as shown in the Purging events automatically
section?
• Is there a specific event in the query that is making up a majority of your events?
Remember, it's very common to forget to include a purge task. This causes ePolicy Orchestrator to
retain every single event since the McAfee ePO server was built. You can fix this simply by creating
a purge task. See Purge events by query for details.
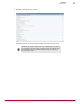
But, if you notice one or two events make up a disproportionate number of your events then
determine what they are by drilling down into those events. For example, in the previous figure you
see that the event with the most instances is an access protection rule from VirusScan Enterprise.
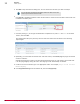
This is a very common event. If you double-click on the Access Protection rule event to drill down
on the cause you can see in the following figure. You find there a few access protection rules that
are being triggered repeatedly on VirusScan Enterprise.
10
At this point determine if these are important events in your organization, or if they are even being
looked at by administrators. Ignoring some events is very common by some administrators.
Ultimately, whenever dealing with excessive events in your database you must follow this process:
1
Create a query showing all events you are questioning using the information in this section to
analyze these threat events.
2
Determine if anyone is looking at these excessive events in the first place
3
If events are not being analyzed, change your policy to stop the event forwarding
11
Reporting
Custom queries
94
McAfee
®
ePolicy Orchestrator
®
4.0 and 4.5 Best Practices Guide