Product guide
Table Of Contents
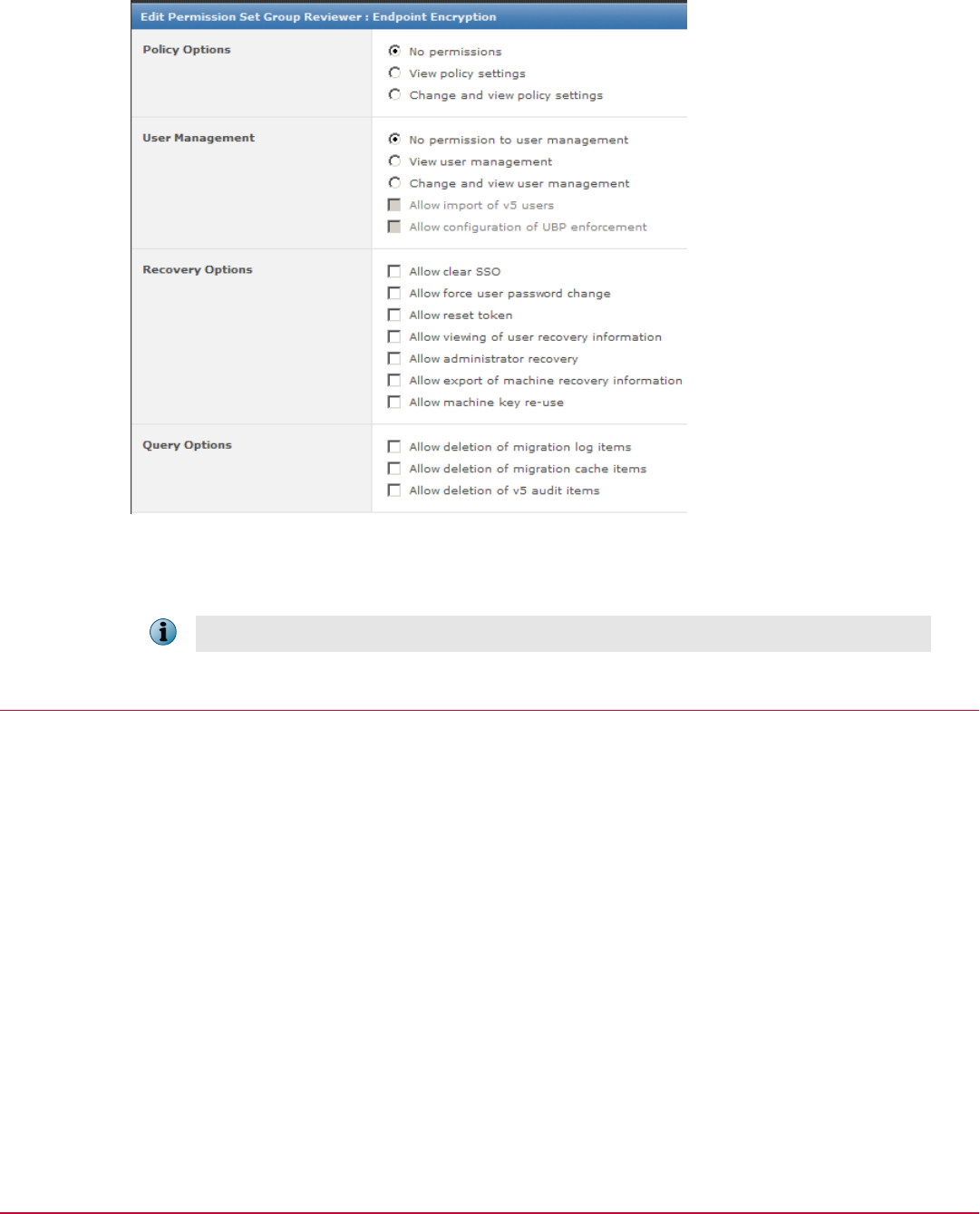
You can create different permission roles and assign them with different Endpoint Encryption Permission Sets
to different users.
Figure 5-1 Endpoint Encryption permission sets
To verify the configured permission sets, log off from ePolicy Orchestrator, then log on with a user
account that belongs to any one of the new roles.
Use correct format of the user name (domain\username) when logging on to ePolicy Orchestrator.
EEPC 7.0 Patch 1 scalability
Use these configurations, recommendations on components, and considerations for scalability.
• ePolicy Orchestrator 4.6 Patch 4
• EEPC 7.0 Patch 1
These considerations and settings will help improve scalability:
Operations and maintenance
EEPC 7.0 Patch 1 scalability
5
McAfee Endpoint Encryption 7.0 Patch 1 Software Best Practices Guide
49










