Product guide
Table Of Contents
Task
1
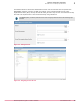
Click Menu | Reporting | Queries. The Queries page opens.
2
Select Endpoint Encryption from Shared Groups in Groups pane. The standard EE query list appears.
3
Run the EE: Users query to list all the Endpoint Encryption Users.
4
Select a user(s) from the list to enforce the policy.
5
Click Actions | Endpoint Encryption | Configure UBP enforcement. The Configure UBP enforcement page
appears with Enable and Disable options.
6
Select Enable or Disable, then click OK to configure the UBP enforcement state. On selecting Enable,
Policy Assignment Rules are enabled for the selected users, and a specific UBP is assigned to the
user according to the rule defined.
At each ASCI, ePolicy Orchestrator enforces all the relevant user‑based policies to each client in
addition to the user‑based policy for the logged on user configured with UBP enforcement.
PBA in Endpoint Encryption 7.0 Patch 1
On BIOS‑based systems, the EEPC operating system provides security by booting prior to Windows
and requiring Pre‑Boot Authentication before the user is allowed to access the main operating system.
On UEFI‑based systems, the EEPC software runs as a trusted application providing the same level of
functionality.
PBA in EEMac is a firmware application that acts as a trusted authentication layer by serving as an
extension of the boot firmware and guarantees a secure, tamper‑proof environment external to the
Mac operating system. Firmware is the combination of persistent memory and program code and data
stored in it.
The PBA in Endpoint Encryption prevents Windows or Mac from loading until the user has
authenticated with the correct password. It eliminates the possibility that one of the millions of lines of
the OS code can compromise the privacy of personal or company data.
The PBA provided by Endpoint Encryption has proven time and time again as the best Data Protection
solution in the market. The PBA solution is an unmatched best practice to be followed by any
organization for system security and data protection.
Design overview
PBA in Endpoint Encryption 7.0 Patch 1
2
McAfee Endpoint Encryption 7.0 Patch 1 Software Best Practices Guide
11