Product guide
5
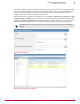
Click Actions | Endpoint Encryption | Configure UBP enforcement. The Configure UBP enforcement page
appears with Enable and Disable options.
6
Select Enable or Disable, then click OK to configure the UBP enforcement state. On selecting Enable,
Policy Assignment Rules are enabled for the selected users, and a specific UBP is assigned to the
user according to the rule defined.
At each ASCI, ePolicy Orchestrator enforces all the relevant user-based policies to each client in
addition to the user-based policy for the logged on user configured with UBP enforcement.
PBA in EEPC 6.2
PBA in EEPC is part of a mini operating system that acts as a trusted authentication layer by serving
as an extension of the BIOS, or boot firmware, and guarantees a secure, tamper-proof environment
external to the Microsoft Windows operating system.
The PBA prevents Windows from loading until the user has authenticated with the correct password. It
eliminates the possibility that one of the millions of lines of the OS code can compromise the privacy
of personal or company data.
The PBA provided by EEPC has proven time and time again as the best Data Protection solution in the
market. The PBA solution is an unmatched best practice to be followed by any organization for system
security and data protection.
How Endpoint Encryption works
A boot sequence is executed by the BIOS leading to the starting of the bootable operating systems.
The boot sequence is the initial set of operations that the computer performs when it is switched on. A
boot loader (or a bootstrap loader) is a short computer program that loads the main operating system
for the computer. The BIOS first looks at a boot record, which is the logical area zero (or starting point)
point of the disk drive, known as Master Boot Record (MBR), which contains the boot loader.
EEPC alters the MBR; the BIOS loads the modified MBR that will then load the sector chain containing
the Pre-Boot environment. This Pre-Boot screen then prompts the user for authentication credentials,
which might be a password, smart card, or token.
After the user enters valid authentication credentials, the operating system starts to load and the user
can use the computer in a normal way.
Encrypting a PC with EEPC 6.2 is the best and the most important practice that any organization can
have for protecting their data.
McAfee ePO requirements
The McAfee ePO server is a central store of configuration information for all systems, servers, policies,
and users. It can be installed only on Windows Server 2003 or 2008 operating systems. For detailed
Design philosophy
PBA in EEPC 6.2
2
McAfee Endpoint Encryption for PC 6.2 Software Best Practices Guide
11