Lake Controller Operation Manual
Table Of Contents
- 1. Welcome
- 2. Software Installation
- 3. Network & Firewall Overview
- 4. Lake Controller Tutorial
- 5. Home Menu Reference
- 6. EQ/Levels Menu Reference
- 7. System Store Recall Menu Reference
- 8. Modules Menu Reference
- 10. Groups Menu Reference
- 11. Solo/Mute Menu Reference
- 12. Icon Control Menu Reference
- 13. User Preferences Menu Reference
- 14. Pages Menu Reference
- 15. Network Menu Reference
- 16. Communication and Synchronization
- 17. Faults and Warnings
- 18. Analyzer Plug-in
- 19. Designer Mode Menu Reference
- 20. Lake-enabled Amplifier Reference
- 21. LM Series Reference and Operation
- 22. MY8-LAKE Reference and Operation
- 23. Keyboard Shortcuts
- 24. External Control Interfaces
- 25. Command Line Options
- 26. Firmware Update
- 27. Preset Manager
- 28. IP Address Reference
- 29. Corporate Information
20
Lake Controller Operation Manual Rev 1.5.9
Network & Firewall Overview
Figure 3-10: Basic Wireless Setup (Not Suitable for Use with Dante or larger networks)
Ideally, the procedure just described yields a perfectly functional and secure system. However, there are
two complications: Some environments have additional wireless network systems and communications
equipment competing for the same airspace used by the Lake system. It is also important to provide secu-
rity so another wireless network cannot access this network system.
As part of the 802.11 standard, various levels of access control and encryption exist. There are also different
communication channels that operate at different frequencies.
The service set identier (SSID) controls access to this wireless network by functioning as a password or
key between wireless network devices to differentiate them from each other. The SSID must be exactly the
same on all wireless devices (the access point and all Controller host computers). The SSID is case sensi-
tive.
Although the SSID differentiates among wireless systems, it does not provide security to the network.
Wired Equivalent Privacy (WEP) is a security protocol for wireless networks dened in the 802.11 standard.
The WEP protocol provides the same level of security as a wired network by encrypting data over radio
waves to protect it during transmission. It is recommend that WEP encryption is enabled if other computers
are connected to your Ethernet network.
3.5.2 Conguring the Tablet PC for Wireless Networking
Assuming that the wireless access point has been set up appropriately and is turned on, we now need to
congure the Tablet PC to connect to this access point.
1. Navigate to the Windows Network and Sharing Center as shown in Figure 3-4.
2. Tap the wireless signal strength icon at the bottom-right of the screen in the Windows notications
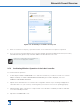
area and select the wireless access point from the list that appears and tap CONNECT as shown in
Figure 3-11.