User Guide
Table Of Contents
- KASPERSKY ANTI-VIRUS FOR PROXY SERVER
- OPERATION ALGORITHM AND TYPICAL DEPLOYMENT SCENARIOS
- INSTALLING THE APPLICATION
- USING KASPERSKY ANTI-VIRUS
- ADDITIONAL SETTINGS OF KASPERSKY ANTI-VIRUS
- Creating groups
- Anti-virus scan settings
- The choice of actions over scanned objects
- Administrator notifications
- Operation modes
- Modes of interaction with proxy via ICAP
- Application statistics logging
- Application reporting parameters
- Memory dump creation for detection of errors
- Work with Internet broadcasting stations
- UNINSTALLING THE APPLICATION
- APPLICATION REFERENCE
- KASPERSKY LAB
- LICENSE AGREEMENT
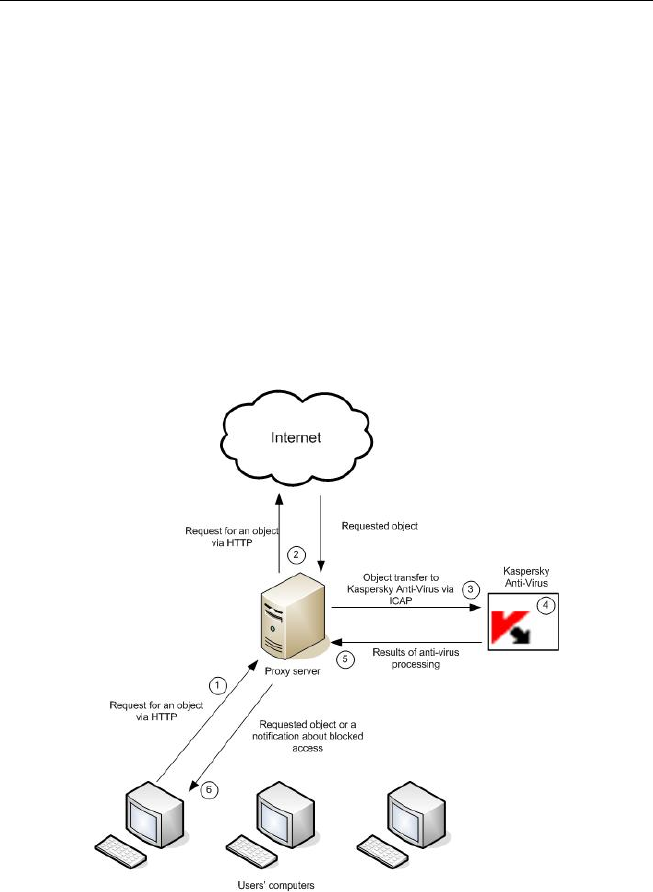
Operation algorithm and typical deployment scenarios 11
existing groups, the application will use the default group rules for
anti-virus scanning and processing.
5. The application uses the results of anti-virus scanning to assign to
a scanned object a specific status, which is employed to grant
users access to that object or block access attempts (please refer
to section 5.3 on p. 36 for details about available statuses and
actions performed by the application). Access to objects with a
specific status is granted or blocked according to the processing
group parameters (please refer to section 5.1 on p. 34 for details
about groups).
6. If access to an object has been granted, Kaspersky Anti-Virus
allows Squid proxy to cache the object and transmit it to users. If
access to an object is blocked, Kaspersky Anti-Virus prohibits
Squid proxy to cache the object and deliver it to users. Instead of
the requested object, the user will receive a notification informing
that access to that object has been blocked.
Figure 1. Anti-virus scanning of traffic in the RESPMOD mode










