manual
Table Of Contents
- Introduction
- Scope
- Design Considerations—Connectivity at the Branch Office
- Branch-Office Connectivity over IPsec VPN
- Design Recommendations
- Routing Information Protocol
- Traffic Load Balancing for Type B and Type C Branch Deployments
- Using Border Gateway Protocol for Large Networks
- Using OSPF for Small Number of Branch Offices
- Using Auto Connect VPN to Create Branch-to-Branch IPsec Tunnels
- High Availability for the Branch Office
- High Availability Requirement Levels (Link, Device, Device, and Link Levels)
- High Availability Functionalities
- High Availability for Branch Office Type A
- VPN Security Zone Configuration for Type A
- High Availability for Branch Office Type B
- Using Secure Services Gateway for Type B
- High Availabilty for Branch Office Type C
- Connectivity at the Data Center
- Implementing a High Availability Enterprise Network at the Data Center
- Quality of Service Design Requirements
- WX Design Requirements
- Summary
- Appendix A Related Documents
- Appendix B Naming Conventions
- Appendix C Products
- About Juniper Networks
- Figure 1: Connecting branch offices, campus locations, and data centers over a single converged network
- Figure 2: Branch office reference architecture
- Figure 3: Multi-tiered/layered network architecture
- Figure 4: Two-tier network design for data centers
- Figure 5: Branch with dual internet connections (load balancing using ECMP)
- Figure 6: BGP routing design
- Figure 7: Star topology – connecting branches to central hub
- Figure 8: AC VPN provisioned tunnels between branches in the same region
- Figure 9: Multi-tier topology
- Figure 10: HA configuration for Type A
- Figure 11: VPN security zone configuration for Type A
- Figure 12: Type B optimized – HA configuration
- Figure 13: Type B – security zones
- Figure 14: Type C – HA configuration
- Figure 15: Intra-branch using OSPF
- Figure 16: Branch Type C – security zones
- Figure 17: Enterprise network for the data center
- Figure 18: M Series Multiservice Edge Routers
- Figure 19: Internet firewalls
- Figure 20: VPN firewalls
- Figure 21: VPN firewall IPS policy
- Figure 2: Branch office reference architecture
18 Copyright © 2010, Juniper Networks, Inc.
APPLICATION NOTE - Branch Office Connectivity Guide
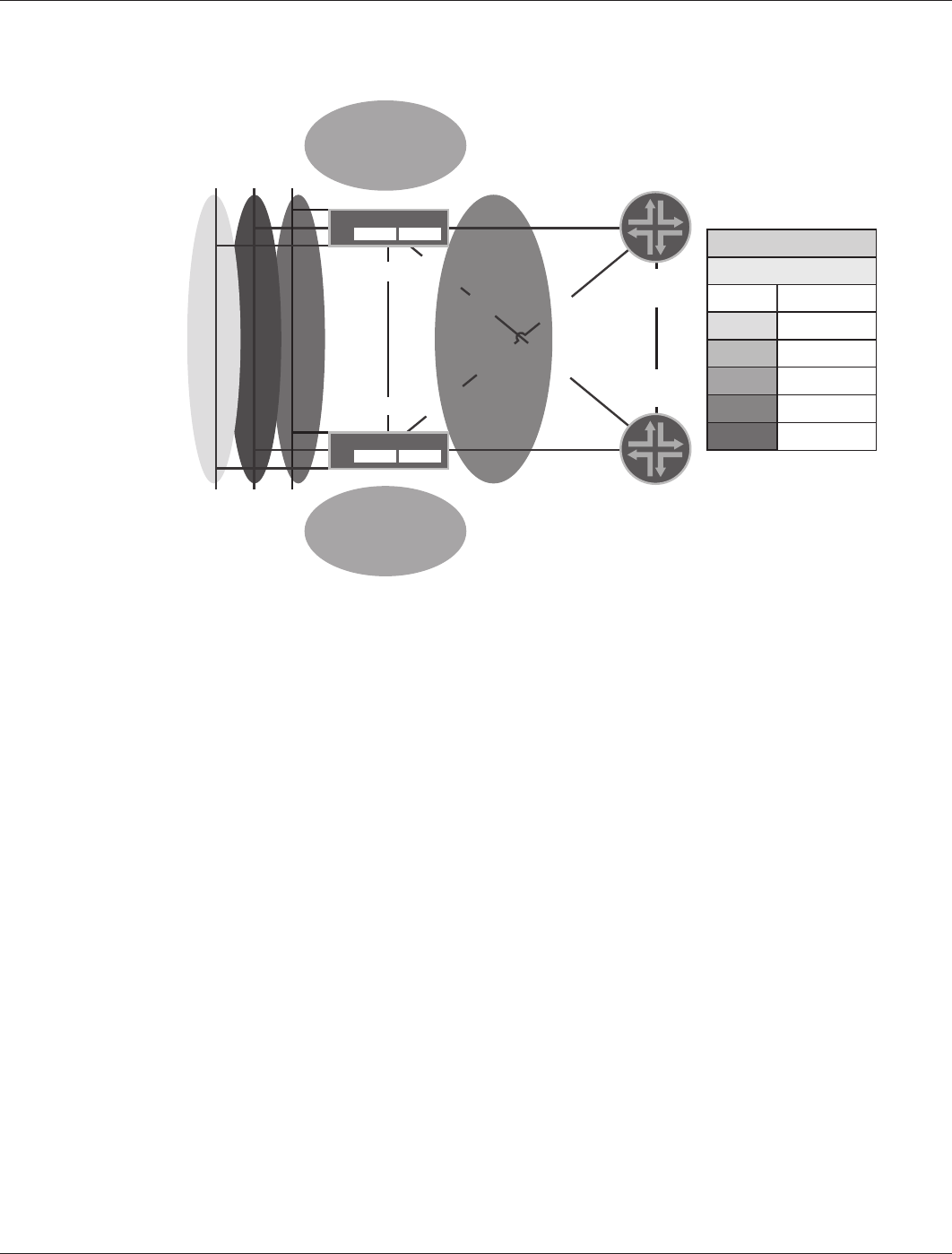
Pertaining to the other branch offices, the interfaces facing the J Series routers and the loopback interfaces are part
of the untrust zone, the tunnel interfaces are part of the VPN zone, and the guest and user-facing interfaces are part
of the guest and trust zones, respectively. See Figure 16.
Figure 16: Branch Type C – security zones
Under typical network conditions, IPsec tunnels terminate on the SSG Series (A). In the event of a failure, the VSIs on
the SSG Series (B) become active (for instance, if the interface Ethernet 0/9:1 that connects to the trust zone fails).
The IPsec tunnels then terminate on the SSG Series (B) because OSPF advertises this device as hosting the VSI
interfaces. The configuration of the SSG Series (B) is similar to the SSG Series (A), except for the NSRP priorities for
the VSD group they share—where the SSG Series (A) is preferred—and their interface addresses.
For deploying HA at branch office Type C, see Implementing High Availability at the Branch Office. In addition, Appendix
C presents the product tables for the various Juniper Networks and Juniper partner product solutions that support
the design and deployment of high-performance enterprise networks.
Connectivity at the Data Center
Accommodating secure branch office connectivity requires a corresponding data center solution that offers
HA, supports IPsec VPN connectivity, and delivers assured network performance and manageability across the
enterprise. The data center design must support branch office connectivity while ensuring business continuity for the
entire enterprise.
Implementing a High Availability Enterprise Network at the Data Center
This section offers design guidance and practices for implementing a resilient central edge design that contains
no single point of failure and consists of a fully meshed, redundant active/active high availability deployment. This
section also provides Juniper’s design practices and recommendations for creating an agile and highly available
network at the data center. While this design primarily focuses on the firewall deployment, it also describes other
elements needed to design a highly available network infrastructure at the data center.
Design Requirements
Juniper Networks Enterprise Framework and Branch Office Reference Architecture documents provide the framework
for this solution. Table 3 summarizes the key design requirements. The requirements are grouped by functionality,
which further describes the design criteria for implementing this high availability network deployment.
1.140.1.0/24
1.140.0.0/24
192.168.10.0/24
HA-link
e0/9:1
e0/8:1
e0/1:1
e0/9:1
e0/8:1
e0/1:1
SSG Series
SSG Series
172.18.140.2
172.18.140.17
ge-0/0/3
172.18.140.17
ge-0/0/3
loopback.1:1 172.18.1.3/32
loopback.2:1 1.4.17.24/32
loopback.1:1 172.18.1.3/32
loopback.2:1 1.4.17.24/32
s1/0
172.18.140.6
e0/0
172.18.140.1
172.18.140.5
ge-0/0/1
Tunnel.1 10.255.1.20
Tunnel.2 10.255.5.20
Tunnel.1 10.255.1.20
Tunnel.2 10.255.5.20
Legend
Zone
Color Description
DMZ
VPN
Untrust
Trust
Guest
e0/4
e0/4
172.18.140.14
e0/2
172.18.140.9
ge-0/0/2
172.18.140.10
e0/2
172.18.140.13
ge-0/0/2
J Series (A)
J Series (B)










