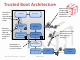
Deploying Secure Boot: Key Creation and Management
Checklist
Define your security strategy
Identify roles
Procure server and hardware for key management
• Recommended solution – network or standalone HSM
• Consider whether you will need one or several HSM’s for high availability and
also your key back up strategy
Set policy for how frequently will you be rekeying keys
Have a contingency plan for Secure Boot Key compromise
Identify how many PK and other keys will you be generating
Use HSM to pre-generate secure boot related keys and certificates
Get the Microsoft KEK and other Secure Boot related keys and
certificates
Sign UEFI drivers
Update firmware with Secure Boot keys based on the system type
Run tests including WHCK Secure Boot tests
Deploy > Refine > Deploy > Refine…
12 UEFI Summer Summit – July 2012 www.uefi.org