Security Solutions
3-92
Designing Access Controls
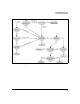
Choose RADIUS Servers
The numbered decision points in the tree are discussed in the next few
paragraphs.
1. Have you chosen an access control component combination with inte-
grated servers?
You must, of course, choose PEPs with that capability. Then answer these
questions:
a. Do you store credentials in another directory, such as OpenLDAP or
eDirectory?
If you want to use an integrated server, such as the AP 530’s RADIUS
server, which cannot bind to a directory, you must add a proxy server
such as SBR or a NAC 800. Move to step 2 to choose the server.
b. Do you want to use IDM?
If your integrated server does not support the IDM agent, you must
add a proxy server that does. Move to step 2 to choose the server.
c. Do some PEPs (such as switches) not provide an integrated server?
If your integrated server is the Wireless Edge Services Module, its
built-in server can receive authentication requests from other PEPs.
Otherwise, you should add another proxy server.
If you do not require integrated servers or you need a proxy server, answer
the questions below to choose the server.
2. Do you store credentials in Active Directory?
If so, you should generally use IAS, which is designed to synchronize with
Active Directory.
3. Do you plan to use MAC-Auth?
If not, move to step 4.
If you do, it is recommended that you do not use Microsoft’s IAS with
MAC-Auth in a Windows domain for two reasons:
• Using MAC-Auth with IAS requires creation of pseudo-user accounts
(consisting of the allowable MAC addresses) on the Active Directory
service. This approach pollutes the Active Directory service with
unnecessary accounts.
• Adding MAC addresses as pseudo-user accounts in Active Directory
can compromise security if configuration is not clean and if users
begin using MAC addresses as login credentials.
You can avoid these problems by using the NAC 800 or a third-party
RADIUS server to locally administer MAC addresses and to service the
RADIUS requests coming from the network edge.