Configuring and Managing Host-Based X.25 Links - Edition 6 (36939-90057)
Introduction
Connections via PAD Support
Chapter 1
22
appear in the node names list can appear in an access list. The name can be an NS
nodename or an IP address. You may have to enter more than one “version” of the same
address, for example both the IP address and the Internet Services address of the same
device, to allow users to enter either, and still gain access.
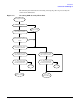
When a remote PAD terminal calls into the DTC to connect to a local system, the DTC
looks up the calling address in the PAD Incoming Security table. The call is accepted if
the called host system is included in an access list defined for the calling address. A
password may optionally be defined for each access list, in which case the PAD terminal
user must also enter the password before the DTC establishes a connection with the
requested host. If the access list corresponding to the calling address is not defined
under PAD Security..., or if it is empty, the incoming call is cleared with CLR DTE 70. By
listing X.25 addresses against non-existent access lists, you can prevent the
corresponding remote devices from accessing any local system nodes.
The lists are downloaded to the DTC when it starts up (after being switched on or reset).
Whenever you make any changes to the list in NMMGR and invoke dynamic
configuration, the updated list is downloaded to all the DTCs that the system is
managing and that have at least one DTC/X.25 Network Access card. Note, however,
that any changes you make to PAD security has no effect on established connections;
lists are checked only while a connection is being established.