Configuring and Managing Host-Based X.25 Links - Edition 6 (36939-90057)
Introduction
Configuring PAD Support and PAD Security
Chapter 1
29
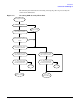
Example of Incoming Security
Figure 1-6 Setting Security Lists
In this example, to connect from terminal 12345601, the remote user can do one of the
following (@ is the PAD prompt, DTC> is the DTC user interface prompt):
PAD Incoming Security
Device X.25 Address Access List Name
12345601 LIST1
12345602 LIST2
Access list: LIST1
NODE1.D.O
128.100.12.3
NODE2.D.O
Node Names list
NODE1.D.O
128.100.12.3
NODE2.D.O
GG3.5.COM
Access List: LIST2
NODE2.D.O
GG3.5.COM
Access list Selection
LIST1
LIST2
The PAD Incoming Security tables maps calling X.25 addresses to access lists
The access lists table
contains he names of all
the access lists defined
for the all X.25 boards
Each access list contains the
names of the hosts which
can be accessed by calling
X.25 addresses mapped to
the list in the PAD Incoming
Security table
The node Names list contains the
names of all the hosts which can
be used in access lists. Only
hosts named in the list can be
entered in access lists
NODE1.D.O
GG3.5.COM
NODE2.D.O
128.100.12.3
X.25
2335A
private
PAD
@12345601
@12345602
X.25
DTC