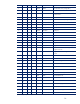
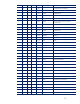
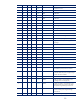
Managing HP Servers through Firewalls with Insight Management 7.0
17
Inbound (in) – Request or response received by a server is called inbound
1
All ports are for TCP (except ICMP and SNMP).
2
The CMS will normally have all managed system ports open, as the CMS is a managed system itself. Firewalls may be
configured to block these ports if the CMS is not to be managed from another system.
3
RMI port is used within the CMS for inter-process communication. Connections from outside the CMS are not accepted, and
firewalls may block this port.
4
Many CMS outgoing ports are used for discovery.
5
The exact UDP/TCP ports used by DMI are dynamic and vary from system to system, but they tend to be around 32,780 and
higher.
6
50000 port number is configurable in server.xml (see Appendix B: Modifying default ports).
7
50004 port number is configurable in globalsettings.props (see Appendix B: Modifying default ports).
Version Control
This discussion is based on the assumption that the Version Control Repository (VCR) is behind the
firewall with CMS, and likely on the CMS.
Discovering the software available on the managed system requires SNMP over port 161. After
receiving a command to update some component, the system must retrieve the component from the
VCR, which it does using HTTPS over port 2381 to the VCR. To communicate its update status back to
the CMS, the agent uses HTTP over port 280. Additionally, the CMS polls the system for its status
every 15 minutes for up to 2 hours.
Replicate Agent Settings
Replicate Agent Settings require a source system whose configuration is copied and stored at the
CMS for duplicating to other target systems. This function relies on HTTPS traffic via port 2381 and
can operate over the firewall as long as the firewall is configured to pass this traffic.
SSH
SSH is used both locally on the HP SIM central management server and remotely to manage systems
for various tools. Normally, SSH servers listen on TCP port 22. If, for some reason, this must be
changed, the SSH port that HP SIM uses is configurable.
Best Practices
Systems can be made more secure by changing the default settings to the recommended Security
Policies Baselines by ‘Microsoft Security Compliance Manager v. 2.0.20.0’.
Reference:
http://www.microsoft.com/download/en/details.aspx?displaylang=en&id=16776
Below are the summary of the steps to be followed:
• Apply the “Member Server Security Compliance” Baseline Policies for “Windows Server
2008R2Sp1” to the system.
• Open the firewall ports as mentioned in Table 3.
• Install the pre-requisites required for installing IM DVD.
• Install IM DVD.