Software Distributor (SD-UX) Administration Guide HP-UX 11i v1, 11i v2, and 11i v3 (762797-001, March 2014)
Table Of Contents
- Software Distributor Administration Guide
- Contents
- HP secure development lifecycle
- About This Document
- 1 Introduction to Software Distributor
- SD-UX Overview
- SD-UX Concepts
- Using the GUI and TUI Commands
- The Terminal User Interface
- Starting the GUI/TUI Commands
- Window Components
- Opening and closing items in the object list
- Marking Items in the Object List
- Preselecting Host Files
- Software Selection Window
- Session and File Management—The File Menu
- Changing Software Views—The View Menu
- Changing Options and Refreshing the Object List—The Options Menu
- Performing Actions—The Actions Menu
- Getting Help—The Help Menu
- XToolkit Options and Changing Display Fonts
- Working from the Command Line
- 2 Installing Software
- Installation with swinstall
- Features and Limitations
- Installing with the GUI
- Installing from the Command Line
- Installation Tasks and Examples
- Updating to HP-UX 11i
- Installing Patches
- Recovering Updated Files
- Installing Software That Requires a System Reboot
- Using Software Codewords and Customer IDs
- Re-installing Software Distributor
- Installing Multiple Versions
- Installing to an Alternate Root
- Compatibility Filtering and Checking
- Software Selection Checking
- Configuring Your Installation (swconfig)
- Verifying Your Installation (swverify)
- Installation with swinstall
- 3 Managing Installed Software
- 4 Managing Software Depots
- Depot Management Commands and Concepts
- Copying Software Depots
- Registering and Unregistering Depots (swreg)
- Verifying Signed Software Signatures
- Additional Depot Management Tasks and Examples
- Combining Patch Depots
- Creating a Tape Depot for Distribution
- Setting Depot Attributes
- Creating a Network Depot
- Managing Multiple Versions of HP-UX
- Listing Registered Depots
- Listing the Contents of a Depot (swlist -d)
- Source Depot Auditing
- Verifying a Depot (swverify -d)
- Removing Software from Depots
- Removing a Depot
- 5 HP-UX Patching and Patch Management
- 6 Using Jobs and the Job Browser
- 7 Remote Operations Overview
- 8 Reliability and Performance
- 9 SD-UX Security
- 10 Creating Software Packages
- Overview of the Packaging Process
- Identifying the Products to Package
- Adding Control Scripts
- Creating a Product Specification File (PSF)
- Product Specification File Examples
- PSF Syntax
- PSF Object Syntax
- Selecting the PSF Layout Version
- PSF Value Types
- Product Specification File Semantics
- Re-Specifying Files
- Packaging the Software (swpackage)
- Packaging Tasks and Examples
- Registering Depots Created by swpackage
- Creating and Mastering a CD-ROM Depot
- Compressing Files to Increase Performance
- Packaging Security
- Repackaging or Modifying a Software Package
- Packaging In Place
- Following Symbolic Links in the Source
- Generating File Revisions
- Depots on Remote File Systems
- Verifying the Software Package
- Packaging Patch Software
- Writing to Multiple Tapes
- Making Tapes from an Existing Depot
- 11 Using Control Scripts
- Introduction to Control Scripts
- General Script Guidelines
- Packaging Control Scripts
- Using Environment Variables
- Execution of Control Scripts
- Execution of Other Commands by Control Scripts
- Control Script Input and Output
- File Management by Control Scripts
- Testing Control Scripts
- Requesting User Responses (swask)
- Request Script Tasks and Examples
- 12 Nonprivileged SD
- A Command Options
- B Troubleshooting
- Error Logging
- Common Problems
- Cannot Contact Target Host’s Daemon or Agent
- GUI Won’t Start or Missing Support Files
- Access To An Object Is Denied
- Slow Network Performance
- Connection Timeouts and Other WAN Problems
- Disk Space Analysis Is Incorrect
- Packager Fails
- Command Logfile Grows Too Large
- Daemon Logfile Is Too Long
- Cannot Read a Tape Depot
- Installation Fails
- swinstall or swremove Fails With a Lock Error
- Use of Square Brackets ([ and ]) Around an IPv6 Address Causes an Error
- Some SD commands do not work after network configuration changes
- C Replacing or Updating SD-UX
- D Software Distributor Files and File System Structure
- Glossary
- Index
In SD-UX, objects are protected by ACLs. An ACL is a structure, attached to an object, that defines
access permissions for multiple users and groups. It extends the concepts defined by the HP-UX file
system mode bits in two ways: by allowing specification of the access rights of many individuals
and groups instead of just one of each; and by protecting entire SD-UX objects, rather than individual
files.
Generally, a controller requests an agent to perform some operation on a object. SD-UX protects
each host, depot, depot-product, and installation object (root) with an ACL. After a call is
authenticated, the ACL manager is consulted for a caller’s access permissions to a protected object
before allowing the action.
SD-UX authorization uses ACLs to determine the RPC caller’s rights to access a particular SD-UX
object in a particular way (i.e., read, write). An object’s ACL is searched for an entry that matches
the caller. Once a matching entry is found, the permissions granted in that entry are compared to
those required for the operation. If permissions required for the operation are all granted by the
entry, access is authorized, and SD-UX proceeds with the requested operation.
How Agents Handle Controller Requests
When a controller requests an agent to do an operation requiring the participation of another
agent, the two agents must each grant access to the objects under their control before the operation
can complete.
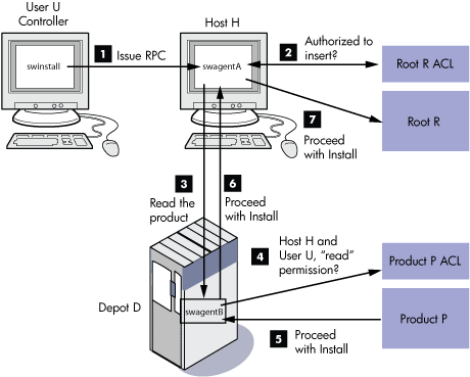
Figure 57 SD-UX Security Process
For example, to install a product P from depot D to root R:
1. User U sends an RPC request to swagentA on the target host H. User U wants to install the
product in root R (on the target host).
2. SwagentA checks the ACL protecting root R to confirm that user U is authorized to insert
products.
3. SwagentA (running as principal H) forms a request to swagentB (running where depot D
resides) to read the product.
4. SwagentB checks the ACL protecting the product to make sure that both the destination system
(principal H) and the user U have read permission before honoring the request, and the
installation proceeds.
The ACL on swagentB neither knows of nor depends on user U. The ACL on root R acts to screen
U; then (and only then) the product’s ACL acts to screen H.
As a special case, the superuser always has full permissions on a local system.
160 SD-UX Security










