Software Distributor (SD-UX) Administration Guide HP-UX 11i v1, 11i v2, and 11i v3 (762797-001, March 2014)
Table Of Contents
- Software Distributor Administration Guide
- Contents
- HP secure development lifecycle
- About This Document
- 1 Introduction to Software Distributor
- SD-UX Overview
- SD-UX Concepts
- Using the GUI and TUI Commands
- The Terminal User Interface
- Starting the GUI/TUI Commands
- Window Components
- Opening and closing items in the object list
- Marking Items in the Object List
- Preselecting Host Files
- Software Selection Window
- Session and File Management—The File Menu
- Changing Software Views—The View Menu
- Changing Options and Refreshing the Object List—The Options Menu
- Performing Actions—The Actions Menu
- Getting Help—The Help Menu
- XToolkit Options and Changing Display Fonts
- Working from the Command Line
- 2 Installing Software
- Installation with swinstall
- Features and Limitations
- Installing with the GUI
- Installing from the Command Line
- Installation Tasks and Examples
- Updating to HP-UX 11i
- Installing Patches
- Recovering Updated Files
- Installing Software That Requires a System Reboot
- Using Software Codewords and Customer IDs
- Re-installing Software Distributor
- Installing Multiple Versions
- Installing to an Alternate Root
- Compatibility Filtering and Checking
- Software Selection Checking
- Configuring Your Installation (swconfig)
- Verifying Your Installation (swverify)
- Installation with swinstall
- 3 Managing Installed Software
- 4 Managing Software Depots
- Depot Management Commands and Concepts
- Copying Software Depots
- Registering and Unregistering Depots (swreg)
- Verifying Signed Software Signatures
- Additional Depot Management Tasks and Examples
- Combining Patch Depots
- Creating a Tape Depot for Distribution
- Setting Depot Attributes
- Creating a Network Depot
- Managing Multiple Versions of HP-UX
- Listing Registered Depots
- Listing the Contents of a Depot (swlist -d)
- Source Depot Auditing
- Verifying a Depot (swverify -d)
- Removing Software from Depots
- Removing a Depot
- 5 HP-UX Patching and Patch Management
- 6 Using Jobs and the Job Browser
- 7 Remote Operations Overview
- 8 Reliability and Performance
- 9 SD-UX Security
- 10 Creating Software Packages
- Overview of the Packaging Process
- Identifying the Products to Package
- Adding Control Scripts
- Creating a Product Specification File (PSF)
- Product Specification File Examples
- PSF Syntax
- PSF Object Syntax
- Selecting the PSF Layout Version
- PSF Value Types
- Product Specification File Semantics
- Re-Specifying Files
- Packaging the Software (swpackage)
- Packaging Tasks and Examples
- Registering Depots Created by swpackage
- Creating and Mastering a CD-ROM Depot
- Compressing Files to Increase Performance
- Packaging Security
- Repackaging or Modifying a Software Package
- Packaging In Place
- Following Symbolic Links in the Source
- Generating File Revisions
- Depots on Remote File Systems
- Verifying the Software Package
- Packaging Patch Software
- Writing to Multiple Tapes
- Making Tapes from an Existing Depot
- 11 Using Control Scripts
- Introduction to Control Scripts
- General Script Guidelines
- Packaging Control Scripts
- Using Environment Variables
- Execution of Control Scripts
- Execution of Other Commands by Control Scripts
- Control Script Input and Output
- File Management by Control Scripts
- Testing Control Scripts
- Requesting User Responses (swask)
- Request Script Tasks and Examples
- 12 Nonprivileged SD
- A Command Options
- B Troubleshooting
- Error Logging
- Common Problems
- Cannot Contact Target Host’s Daemon or Agent
- GUI Won’t Start or Missing Support Files
- Access To An Object Is Denied
- Slow Network Performance
- Connection Timeouts and Other WAN Problems
- Disk Space Analysis Is Incorrect
- Packager Fails
- Command Logfile Grows Too Large
- Daemon Logfile Is Too Long
- Cannot Read a Tape Depot
- Installation Fails
- swinstall or swremove Fails With a Lock Error
- Use of Square Brackets ([ and ]) Around an IPv6 Address Causes an Error
- Some SD commands do not work after network configuration changes
- C Replacing or Updating SD-UX
- D Software Distributor Files and File System Structure
- Glossary
- Index
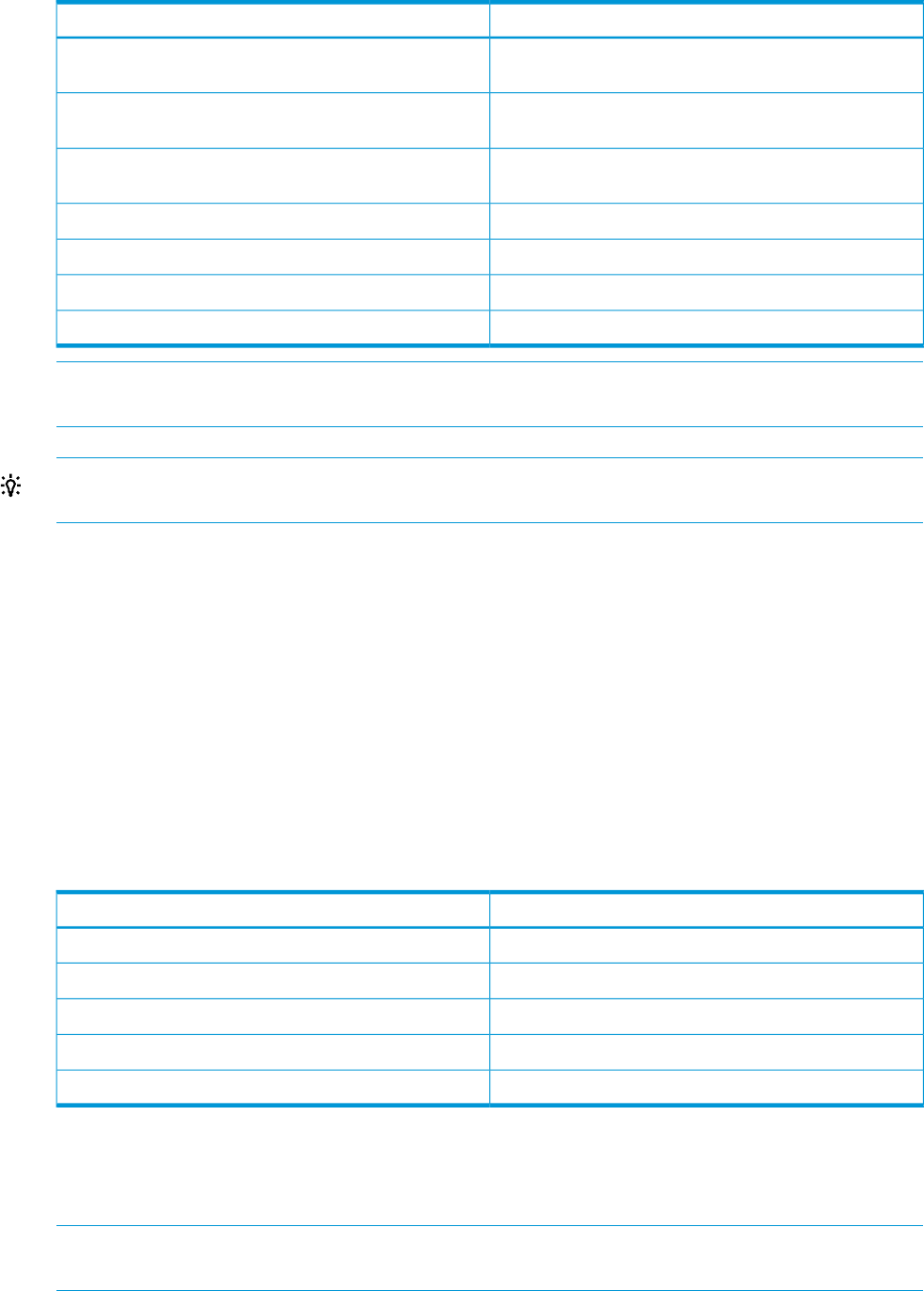
Table 36 SD-UX ACL Entry Types
Permissions Apply ToType
User principal, whose name is to be specified in the key
field
user
Group principal, whose name is to be specified in the key
field
group
Host systems (target agents acting on behalf of users for
install or copy)
host
Principals with no matching user and group entriesother
Principals not matching any other entryany_other
Owner of the objectobject_owner
Members of the group to which an object belongsobject_group
NOTE: The host cannot be specified in the IPv6 format. This feature is not supported in ACL
entries.
TIP: Do not confuse the host object (which is a computer system that contains depots, roots, and
software) with the host entry type (which defines permissions for access to target systems).
The user and group of the object’s owner are determined and automatically recorded at the time
the object is created (based on the identity of the person who creates it). This information is recorded
as user, group, and realm. An object_owner or object_group entry type in an ACL
causes the SD-UX ACL manager to look up the owner and group information on the object; and if
a match to the requester is found, grant permissions as specified.
There may be many user, group, and host type entries per ACL, while there may be only one
of each of object_owner, object_group and any_other. There may be at most one local
(i.e., no key) other entry and an unlimited number of remote (i.e., keyed) other entries.
ACL Keys
The second part of the ACL entry is the key. The table below lists the possible key values for specific
entry types.
Table 37 SD-UX ACL Entry Key Values
Key ContentEntry Type
a user name [optionally, @ remote-host]user
a group name [optionally, @ remote-host]group
a host namehost
[optionally, @ remote-host]other
no key allowedany_other
When listing the ACL, the remote-host is printed in its Internet address form (e.g., 15.12.89.10)
if the local system cannot resolve the address from its host lookup mechanism (DNS, NIS, or
/etc/hosts). The remote-host must be recognized (resolvable) when used in the -M and -D
options. Unrecognized remote-host values are accepted in files provided with the -F option.
NOTE: The remote-host cannot be specified in IPv6 format. This feature is not supported in ACL
entries.
ACL Entries 151










