Software Distributor Administration Guide (March 2009)
Table Of Contents
- Software Distributor Administration Guide
- Table of Contents
- About This Document
- 1 Introduction to Software Distributor
- 1.1 SD-UX Overview
- 1.2 SD-UX Concepts
- 1.3 Using the GUI and TUI Commands
- 1.3.1 The Terminal User Interface
- 1.3.2 Starting the GUI/TUI Commands
- 1.3.3 Window Components
- 1.3.4 Opening and closing items in the object list
- 1.3.5 Marking Items in the Object List
- 1.3.6 Preselecting Host Files
- 1.3.7 Software Selection Window
- 1.3.8 Session and File Management—The File Menu
- 1.3.9 Changing Software Views—The View Menu
- 1.3.10 Changing Options and Refreshing the Object List—The Options Menu
- 1.3.11 Performing Actions—The Actions Menu
- 1.3.12 Getting Help—The Help Menu
- 1.3.13 XToolkit Options and Changing Display Fonts
- 1.4 Working from the Command Line
- 2 Installing Software
- 2.1 Installation with swinstall
- 2.1.1 Features and Limitations
- 2.1.2 Installing with the GUI
- 2.1.3 Installing from the Command Line
- 2.1.4 Installation Tasks and Examples
- 2.1.4.1 Updating to HP-UX 11i
- 2.1.4.2 Installing Patches
- 2.1.4.3 Recovering Updated Files
- 2.1.4.4 Installing Software That Requires a System Reboot
- 2.1.4.5 Using Software Codewords and Customer IDs
- 2.1.4.6 Re-installing Software Distributor
- 2.1.4.7 Installing Multiple Versions
- 2.1.4.8 Installing to an Alternate Root
- 2.1.4.9 Compatibility Filtering and Checking
- 2.2 Configuring Your Installation (swconfig)
- 2.3 Verifying Your Installation (swverify)
- 2.1 Installation with swinstall
- 3 Managing Installed Software
- 3.1 Listing Your Software (swlist)
- 3.1.1 swlist Features and Limitations
- 3.1.2 Using the swlist GUI
- 3.1.3 Using the Command Line
- 3.1.4 Software Listing Tasks and Examples
- 3.2 Modifying the IPD (swmodify)
- 3.3 Removing Installed Software (swremove)
- 3.1 Listing Your Software (swlist)
- 4 Managing Software Depots
- 4.1 Depot Management Commands and Concepts
- 4.2 Copying Software Depots
- 4.3 Registering and Unregistering Depots (swreg)
- 4.4 Additional Depot Management Tasks and Examples
- 4.4.1 Combining Patch Depots
- 4.4.2 Creating a Tape Depot for Distribution
- 4.4.3 Setting Depot Attributes
- 4.4.4 Creating a Network Depot
- 4.4.5 Managing Multiple Versions of HP-UX
- 4.4.6 Listing Registered Depots
- 4.4.7 Listing the Contents of a Depot (swlist -d)
- 4.4.8 Source Depot Auditing
- 4.4.9 Verifying a Depot (swverify -d)
- 4.4.10 Removing Software from Depots
- 4.4.11 Removing a Depot
- 5 HP-UX Patching and Patch Management
- 6 Using Jobs and the Job Browser
- 7 Remote Operations Overview
- 8 Reliability and Performance
- 9 SD-UX Security
- 9.1 Overview
- 9.2 The swacl Command
- 9.3 Basic Security Tasks
- 9.4 How ACLs are Matched to the User
- 9.5 ACL Entries
- 9.6 Security on SD-UX Systems
- 9.7 SD-UX Internal Authentication
- 9.8 RPC Authorization
- 9.9 Security Use Models
- 9.10 Permission Requirements, by Command
- 9.10.1 Packaging (swpackage)
- 9.10.2 Listing (swlist)
- 9.10.3 Job Browsing (sd, swjob)
- 9.10.4 Copying (swcopy)
- 9.10.5 Installing (swinstall)
- 9.10.6 Removal (swremove)
- 9.10.7 Configuration (swconfig)
- 9.10.8 Verify (swverify)
- 9.10.9 Registering Depots (swreg)
- 9.10.10 Changing ACLs (swacl)
- 9.10.11 Request Scripts (swask)
- 9.10.12 Modify (swmodify)
- 10 Creating Software Packages
- 10.1 Overview of the Packaging Process
- 10.2 Identifying the Products to Package
- 10.3 Adding Control Scripts
- 10.4 Creating a Product Specification File (PSF)
- 10.4.1 Product Specification File Examples
- 10.4.2 PSF Syntax
- 10.4.2.1 PSF Object Syntax
- 10.4.2.2 Selecting the PSF Layout Version
- 10.4.2.3 PSF Value Types
- 10.4.2.4 Product Specification File Semantics
- 10.4.2.4.1 Vendor-Defined Attributes
- 10.4.2.4.2 Distribution (Depot) Specification
- 10.4.2.4.3 Vendor Specification
- 10.4.2.4.4 Category Specification
- 10.4.2.4.5 Product or Bundle Specification
- 10.4.2.4.6 Control Script Specification
- 10.4.2.4.7 Subproduct Specification
- 10.4.2.4.8 Fileset Specification
- 10.4.2.4.9 Dependency Specification
- 10.4.2.4.10 Control Script Specification
- 10.4.2.4.11 File Specification
- 10.4.2.5 Re-Specifying Files
- 10.5 Packaging the Software (swpackage)
- 10.6 Packaging Tasks and Examples
- 10.6.1 Registering Depots Created by swpackage
- 10.6.2 Creating and Mastering a CD-ROM Depot
- 10.6.3 Compressing Files to Increase Performance
- 10.6.4 Packaging Security
- 10.6.5 Repackaging or Modifying a Software Package
- 10.6.6 Packaging In Place
- 10.6.7 Following Symbolic Links in the Source
- 10.6.8 Generating File Revisions
- 10.6.9 Depots on Remote File Systems
- 10.6.10 Verifying the Software Package
- 10.6.11 Packaging Patch Software
- 10.6.12 Writing to Multiple Tapes
- 10.6.13 Making Tapes from an Existing Depot
- 11 Using Control Scripts
- 11.1 Introduction to Control Scripts
- 11.2 General Script Guidelines
- 11.3 Packaging Control Scripts
- 11.4 Using Environment Variables
- 11.5 Execution of Control Scripts
- 11.5.1 Details Common to All Control Scripts
- 11.5.2 Checkinstall Scripts
- 11.5.3 Preinstall Scripts
- 11.5.4 Postinstall Scripts
- 11.5.5 Configure Scripts
- 11.5.6 Unconfigure Scripts
- 11.5.7 Verify Scripts
- 11.5.8 Fix Scripts
- 11.5.9 Checkremove Scripts
- 11.5.10 Preremove Scripts
- 11.5.11 Postremove Scripts
- 11.5.12 Request Scripts
- 11.6 Execution of Other Commands by Control Scripts
- 11.7 Control Script Input and Output
- 11.8 File Management by Control Scripts
- 11.9 Testing Control Scripts
- 11.10 Requesting User Responses (swask)
- 11.11 Request Script Tasks and Examples
- 12 Nonprivileged SD
- A Command Options
- B Troubleshooting
- B.1 Error Logging
- B.2 Common Problems
- B.2.1 Cannot Contact Target Host’s Daemon or Agent
- B.2.2 GUI Won’t Start or Missing Support Files
- B.2.3 Access To An Object Is Denied
- B.2.4 Slow Network Performance
- B.2.5 Connection Timeouts and Other WAN Problems
- B.2.6 Disk Space Analysis Is Incorrect
- B.2.7 Packager Fails
- B.2.8 Command Logfile Grows Too Large
- B.2.9 Daemon Logfile Is Too Long
- B.2.10 Cannot Read a Tape Depot
- B.2.11 Installation Fails
- B.2.12 swinstall or swremove Fails With a Lock Error
- C Replacing or Updating SD-UX
- D Software Distributor Files and File System Structure
- Glossary
- Index
There may be many user, group, and host type entries per ACL, while there may
be only one of each of object_owner, object_group and any_other. There may
be at most one local (i.e., no key) other entry and an unlimited number of remote (i.e.,
keyed) other entries.
9.5.1 ACL Keys
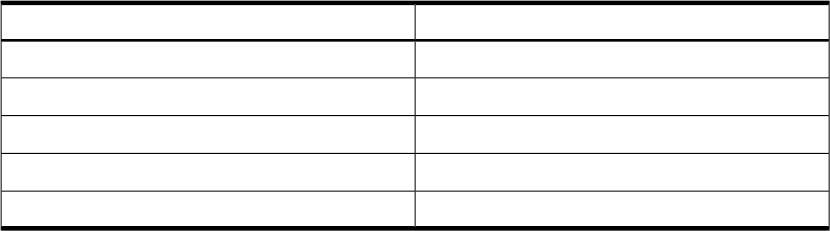
The second part of the ACL entry is the key. The table below lists the possible key
values for specific entry types.
Table 9-4 SD-UX ACL Entry Key Values
Key ContentEntry Type
a user name [optionally, @ remote-host]user
a group name [optionally, @ remote-host]group
a host name
host
[optionally, @ remote-host]other
no key allowed
any_other
When listing the ACL, the remote-host is printed in its Internet address form (e.g.,
15.12.89.10) if the local system cannot resolve the address from its host lookup
mechanism (DNS, NIS, or /etc/hosts). The remote-host must be recognized
(resolvable) when used in the -M and -D options. Unrecognized remote-host values
are accepted in files provided with the -F option.
9.5.2 ACL Permissions
There are five different permissions grantable by the ACL: crwit.
Table 9-5 ACL Permissions
Permission to edit or change the ACL.
control (c)
Permission to test access to an object (i.e., read the ACL).
test (t)
Permission to install a new product, depot or root.
insert (i)
Permission to change a host, depot, root or product.
write (w)
Permission to list depot, roots and products and attributes.
read (r)
In the ACL entry, these permissions are abbreviated c, t, i, w, and r. To grant all
permissions, you may use the shorthand letter a instead of the crwit to denote all
permissions.
The meaning of permissions is different for different types of objects, and the
permissions do not have to appear in any specific order. Roots do not provide product
level protection, so all permissions on products installed on roots are controlled by the
ACL protecting the root itself.
9.5 ACL Entries 197










