Administrator's Guide
2 Product overview
WLI is a security enhancement product that relies on RSA keys and cryptographic algorithms
to restrict access to regular files, directories, and certain protected resources. WLI is complementary
to the traditional access restrictions imposed by file ownership and permission bits. An executable
permitted by WLI to access a file does not bypass permission bit checks, ACLs, or other security
mechanisms.
For more detail on WLI commands and files, see the manpages installed with WLI. For a complete
list of manpages and more technical information, see wli(5).
In discussions involving RSA, “key” is synonymous with “private key” throughout this document,
because a private key holds all key information and the public key is merely a subset.
IMPORTANT: WLI requires OE B.11.31.0909 or later.
For more information, see Section 4.2 (page 21).
IMPORTANT: WLI is supported on VxFS file systems at revision 4.1 or later and on other HP-UX
11iv3 non-VxFS file systems such as HFS.
WLI file access policy enforcement is supported only for regular files and directories residing
on HFS, VxFS, and NFS file systems. Some applications access physical storage directly, bypassing
the supported file systems. Examples are Oracle ASM and Veritas CFS.
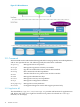
2.1 WLI architecture
For an illustration of WLI architecture, see Figure 2-1 (page 14). WLI commands restrict access
to designated files by generating access policies. Some system resources are also restricted. WLI
kernel software enforces access restrictions by examining policy information in real time during
access requests on files.
2.1 WLI architecture 13