Red Hat Directory Server 8.0 Administrator's Guide
Because Boolean expressions are evaluated from left to right, in the first case, bind rule A is
evaluated before bind rule B, and, in the second case, bind rule B is evaluated before bind rule
A.
However, the Boolean NOT is evaluated before the Boolean OR and Boolean AND. Thus, in the
following example, bind rule B is evaluated before bind rule A despite the left-to-right rule.
(bind_rule_A) AND NOT (bind_rule_B)
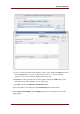
5. Creating ACIs from the Console
You can use the Directory Server Console to view, create, edit, and delete access control
instructions for your directory:
• Section 5.1, “Displaying the Access Control Editor”
• Section 5.2, “Creating a New ACI”
• Section 5.3, “Editing an ACI”
• Section 5.4, “Deleting an ACI”
See Section 9, “Access Control Usage Examples” for a collection of access control rules
commonly used in Directory Server security policies, along with step-by-step instructions for
using the Directory Server Console to create them.
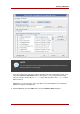
The Access Control Editor prevents creating more complex ACIs in visual editing mode,
especially ACIs with any of these characteristics:
• Deny access (Section 3.3.4, “Permissions Syntax”).
• Create value-based ACIs (Section 3.2.2, “Targeting Attributes”).
• Define parent access (Section 4.2.4, “Parent Access (parent Keyword)”).
• Create ACIs that contain Boolean bind rules (Section 4.10, “Using Boolean Bind Rules”).
• Create ACIs that use the roledn, userattr, authmethod keywords.
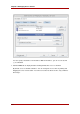
TIP
In the Access Control Editor, click the Edit Manually button at any time to
check the LDIF representation of the ACI changes made through the graphical
interface.
Chapter 6. Managing Access Control
202