LDAP-UX Client Services B.05.01 Administrator Guide for HP directory servers and Windows ADS
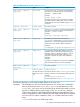
Figure 15 PAM_AUTHZ environment
7
5
6
2
1
3
4
PAM-enabled
application
Policy
configuration
file
PAM_AUTHZ
/etc/group LDAP
directory
server
/etc/netgroup
Authentication
modules, for
example:
PAM_KERBEROS
PAM_LDAP
LDAP_UX
client daemon
ldapclientd
The following describes the PAM_AUTHZ policy validation process for the user login authorization
shown in Figure 15 (page 201):
PAM_AUTHZ environment
1. The administrator defines access rules and saves them in a local access policy configuration
file.
2. PAM_AUTHZ service module receives an authorization request from PAM framework. It processes
all the access rules stored in the access policy configuration file.
3. If a rule indicates that the required information is stored in a LDAP server, PAM_AUTHZ constructs
a request message and sends to the LDAP client daemon, ldapclientd. The LDAP client daemon
performs the actual LDAP query and returns the result to PAM_AUTHZ. Then the access rule is
evaluated and the final access right is returned.
4. If a rule indicates that the required information is in the UNIX files. PAM_AUTHZ retrieves user's
information from /etc/passwd, /etc/group or /etc/netgroup file through getpwname()
or getgrname() system calls. Then the rule is evaluated and the final access right is returned.
5. PAM_AUTHZ returns the corresponding pam result to PAM framework. The decision is returned
to the application which called the PAM API.
6. If the user has the permission to log in, then the decision is returned to the next PAM service
module that is configured in the pam.conf file, such as PAM_LDAP or PAM_KERBEROS. If the
access rule passed but is assigned the required action type, then PAM_AUTHZ continues and
evaluates the next access policy rule. If the access rule failed and is assigned the required action,
or if processing reaches the end of the rules (after they all failed), then login is denied.
7. The PAM service module returns the authentication result to the application that called the PAM
API.
7.4.3 PAM_AUTHZ security policy enforcement
PAM_AUTHZ supports enforcement of account and password policies stored in a directory server.
This feature works with secure shell (ssh) and with r-commands, where rhost is enabled and
authentication is performed by the command itself rather than by the PAM (Pluggable Authentication
Module) subsystem.
7.4 Configuring PAM_AUTHZ login authorization 201