LDAP-UX Client Services B.04.15 with Microsoft Windows Active Directory Server Administrator's Guide (edition 8)
Table Of Contents
- LDAP-UX Client Services B.04.15 with Microsoft Windows Active Directory Administrator's Guide
- Table of Contents
- Preface
- 1 Introduction
- 2 Installing LDAP-UX Client Services
- Before You Begin
- Summary of Installing and Configuring LDAP-UX Client Services
- Planning Your Installation
- Installing LDAP-UX Client Services on a Client
- Configuring Active Directory for HP-UX Integration
- Step 1: Install Active Directory
- Step 2: Install SFU 2.0, 3.0 or 3.5 including Server for NIS
- Step 3: Create a Proxy User
- Step 4: Add an HP-UX Client Machine Account to Active Directory
- Step 5: Use ktpass to Create the Keytab File for the HP-UX client machine
- Step 6: Add POSIX Attributes into the Global Catalog
- Importing Name Service Data into Your Directory
- Configuring LDAP-UX Client Services
- Step 1: Run the Setup Program
- Step 2: Install the PAM Kerberos Product
- Step 3: Configure Your HP-UX Machine to Authenticate Using PAM Kerberos
- Step 4: Configure the Name Service Switch (NSS)
- Step 5: Configure the PAM Authorization Service Module (pam_authz)
- Step 6: Configure the Disable Login Flag
- Step 7: Verify LDAP-UX Client Services for Single Domain
- Step 8: Configure Subsequent Client Systems
- Configuring the LDAP-UX Client Services with SSL or TLS Support
- Downloading the Profile Periodically
- 3 Active Directory Multiple Domains
- 4 LDAP-UX Client Services with AutoFS Support
- 5 LDAP Printer Configurator Support
- 6 Dynamic Group Support
- 7 Administering LDAP-UX Client Services
- Using the LDAP-UX Client Daemon
- Integrating with Trusted Mode
- SASL GSSAPI Support
- PAM_AUTHZ Login Authorization
- Policy And Access Rules
- How Login Authorization Works
- PAM_AUTHZ Supports Security Policy Enforcement
- Policy File
- Policy Validator
- Dynamic Variable Support
- Constructing an Access Rule in pam_authz.policy
- Static List Access Rule
- Dynamic Variable Access Rule
- Security Policy Enforcement with Secure Shell (SSH) or r-commands
- Adding Additional Domain Controllers
- Adding Users, Groups, and Hosts
- User and Group Management
- Displaying the Proxy User's Distinguished Name
- Verifying the Proxy User
- Creating a New Proxy User
- Displaying the Current Profile
- Creating a New Profile
- Modifying a Profile
- Changing Which Profile a Client is Using
- Creating an /etc/krb5.keytab File
- Considering Performance Impacts
- Client Daemon Performance
- Troubleshooting
- 8 Modifying User Information
- 9 Mozilla LDAP C SDK
- A Configuration Worksheet
- B LDAP-UX Client Services Object Classes
- C Command, Tool, Schema Extension Utility, and Migration Script Reference
- LDAP-UX Client Services Components
- Client Management Tools
- LDAP User and Group Management Tools
- Environment Variables
- Return Value Formats
- Common Return Codes
- The ldapuglist Tool
- The ldapugadd Tool
- The ldapugmod Tool
- The ldapugdel Tool
- The ldapcfinfo Tool
- LDAP Directory Tools
- Schema Extension Utility
- Name Service Migration Scripts
- Unsupported Contributed Tools and Scripts
- D Sample PAM Configuration File
- E Sample /etc/krb5.conf File
- F Sample /etc/pam.conf File for HP-UX 11i v1 Trusted Mode
- G Sample /etc/pam.conf File for HP-UX 11i v2 Trusted Mode
- H Sample PAM Configuration File for Security Policy Enforcement
- Glossary
- Index
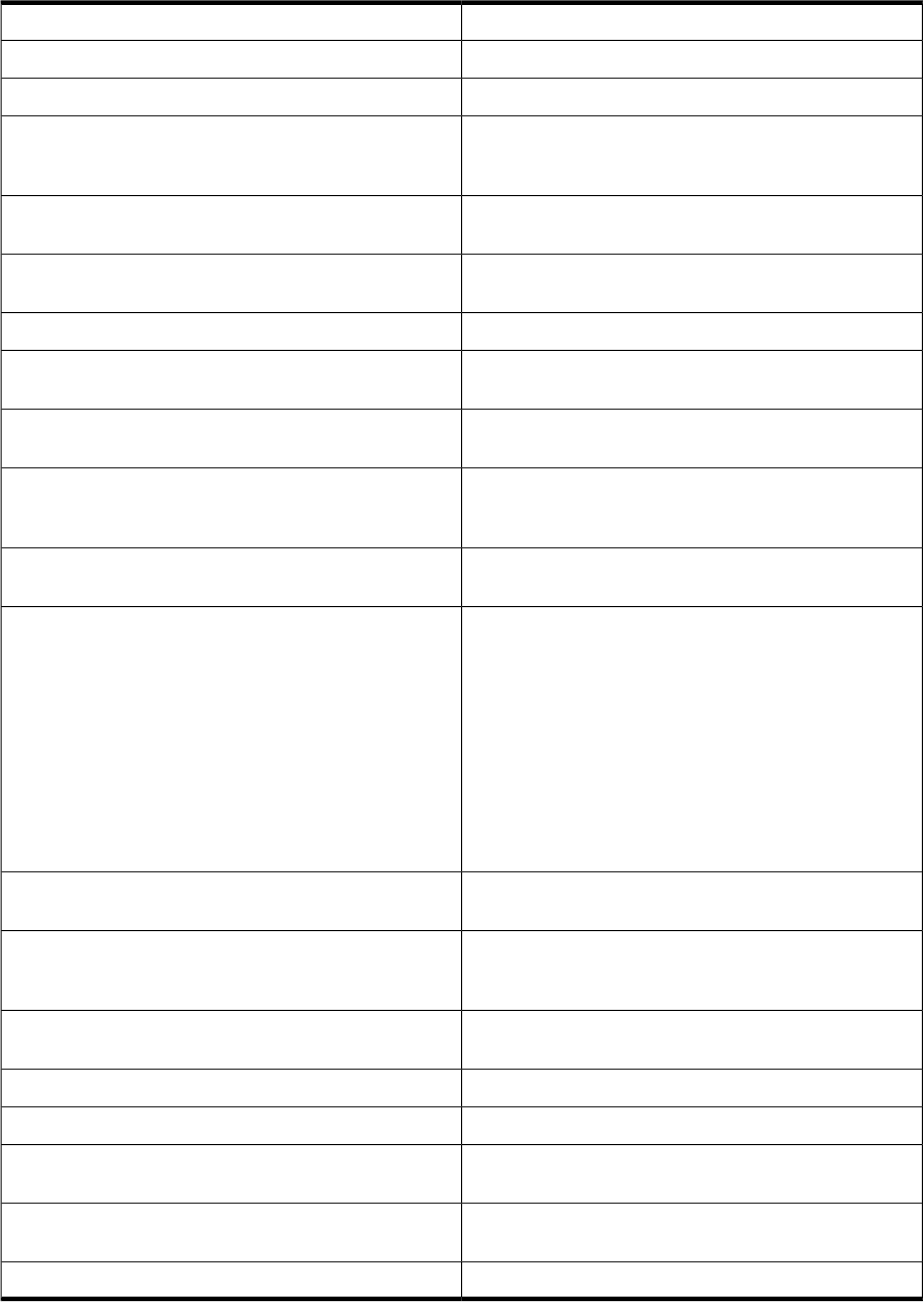
Specific Return Codes for ldapugadd
The ldapugadd tool returns a list of return codes shown in Table C-7.
Table C-7 Return Codes for ldapugadd
MessageReturn Code
Failed to add a user to the group.
ADD_USER_TO_GRP_FAILED
Specified Skeleton directory does not exist.
ADD_SKELDIR_DOESNOT_EXIST
When ldapugadd failed the internal putenv function
call with the specified bind environment variable, it
returns this error.
ADD_SETENV_FAILED
Information is missing. For examples, uid number is
missing, group number is missing.
ADD_INFO_MISSING
Failed to get a valid gid number or uid number when
creating a new user or group entry.
ADD_GETNUM_FAILED
A syntax error exists in the specified template file.
ADD_SYNTAX_ERR
Attribute is required. For examples, attribute “sn” is
required, attribute “telephonenumber” is required.
ADD_ATTR_REQUIRED
Specified option has invalid range value. For example,
option -u has invalid range value.
ADD_NUM_RANGE_ERR
Option -g <default_gid> or -g
<min_gid>:<max_gid> has been specified more than
once.
ADD_WRONG_G_OPT
You do not have the permission to alter
/etc/opt/ldapux/ldapug.conf.
ADD_NOT_PERMIT
The specified keyword value is invalid, ldapugadd
ignored the keyword. For example, if /net/bin/jsh
does not exist in the system, the ldapugadd -D -s
/net/bin/jsh command displays the following
warnings:
WARNING: LOGIN_SHELL_DOESNOT_EXIST:
Login shell /net/bin/jsh' does not exist.
WARNING: ADD_INVALID_KEY
Invalid keyword (default_loginShell),
ignored.
ADD_INVALID_KEYWORD
Failed to rename the internal temporary file to
/etc/opt/ldapux/ldapug.conf.
ADD_RENAME_FAILED
A specific operation has been updated successfully. For
example, “uidnumber_range” defined in ldapug.conf
has been updated successfully.
ADD_UPDATE_OK
Option -m is not specified, therefore, -k ignored when
adding a new account.
ADD_K_IGNORED
DN has been specified more than once.
ADD_TWO_DN_ERR
Options -g and -e cannot be specified at the same time.ADD_GID_GNAME_ERR
The specified group does not exist in the LDAP directory.
Could not add a user to the specified group.
ADD_NOT_IN_LDAP
Failed to update the default value in
/etc/opt/ldapuux_ldapug.conf.
ADD_FAIL_TO_UPDATE
The LDAP add operation failed.
ADD_FAILED
198 Command, Tool, Schema Extension Utility, and Migration Script Reference










