LDAP-UX Client Services B.04.15 with Microsoft Windows Active Directory Server Administrator's Guide (edition 8)
Table Of Contents
- LDAP-UX Client Services B.04.15 with Microsoft Windows Active Directory Administrator's Guide
- Table of Contents
- Preface
- 1 Introduction
- 2 Installing LDAP-UX Client Services
- Before You Begin
- Summary of Installing and Configuring LDAP-UX Client Services
- Planning Your Installation
- Installing LDAP-UX Client Services on a Client
- Configuring Active Directory for HP-UX Integration
- Step 1: Install Active Directory
- Step 2: Install SFU 2.0, 3.0 or 3.5 including Server for NIS
- Step 3: Create a Proxy User
- Step 4: Add an HP-UX Client Machine Account to Active Directory
- Step 5: Use ktpass to Create the Keytab File for the HP-UX client machine
- Step 6: Add POSIX Attributes into the Global Catalog
- Importing Name Service Data into Your Directory
- Configuring LDAP-UX Client Services
- Step 1: Run the Setup Program
- Step 2: Install the PAM Kerberos Product
- Step 3: Configure Your HP-UX Machine to Authenticate Using PAM Kerberos
- Step 4: Configure the Name Service Switch (NSS)
- Step 5: Configure the PAM Authorization Service Module (pam_authz)
- Step 6: Configure the Disable Login Flag
- Step 7: Verify LDAP-UX Client Services for Single Domain
- Step 8: Configure Subsequent Client Systems
- Configuring the LDAP-UX Client Services with SSL or TLS Support
- Downloading the Profile Periodically
- 3 Active Directory Multiple Domains
- 4 LDAP-UX Client Services with AutoFS Support
- 5 LDAP Printer Configurator Support
- 6 Dynamic Group Support
- 7 Administering LDAP-UX Client Services
- Using the LDAP-UX Client Daemon
- Integrating with Trusted Mode
- SASL GSSAPI Support
- PAM_AUTHZ Login Authorization
- Policy And Access Rules
- How Login Authorization Works
- PAM_AUTHZ Supports Security Policy Enforcement
- Policy File
- Policy Validator
- Dynamic Variable Support
- Constructing an Access Rule in pam_authz.policy
- Static List Access Rule
- Dynamic Variable Access Rule
- Security Policy Enforcement with Secure Shell (SSH) or r-commands
- Adding Additional Domain Controllers
- Adding Users, Groups, and Hosts
- User and Group Management
- Displaying the Proxy User's Distinguished Name
- Verifying the Proxy User
- Creating a New Proxy User
- Displaying the Current Profile
- Creating a New Profile
- Modifying a Profile
- Changing Which Profile a Client is Using
- Creating an /etc/krb5.keytab File
- Considering Performance Impacts
- Client Daemon Performance
- Troubleshooting
- 8 Modifying User Information
- 9 Mozilla LDAP C SDK
- A Configuration Worksheet
- B LDAP-UX Client Services Object Classes
- C Command, Tool, Schema Extension Utility, and Migration Script Reference
- LDAP-UX Client Services Components
- Client Management Tools
- LDAP User and Group Management Tools
- Environment Variables
- Return Value Formats
- Common Return Codes
- The ldapuglist Tool
- The ldapugadd Tool
- The ldapugmod Tool
- The ldapugdel Tool
- The ldapcfinfo Tool
- LDAP Directory Tools
- Schema Extension Utility
- Name Service Migration Scripts
- Unsupported Contributed Tools and Scripts
- D Sample PAM Configuration File
- E Sample /etc/krb5.conf File
- F Sample /etc/pam.conf File for HP-UX 11i v1 Trusted Mode
- G Sample /etc/pam.conf File for HP-UX 11i v2 Trusted Mode
- H Sample PAM Configuration File for Security Policy Enforcement
- Glossary
- Index
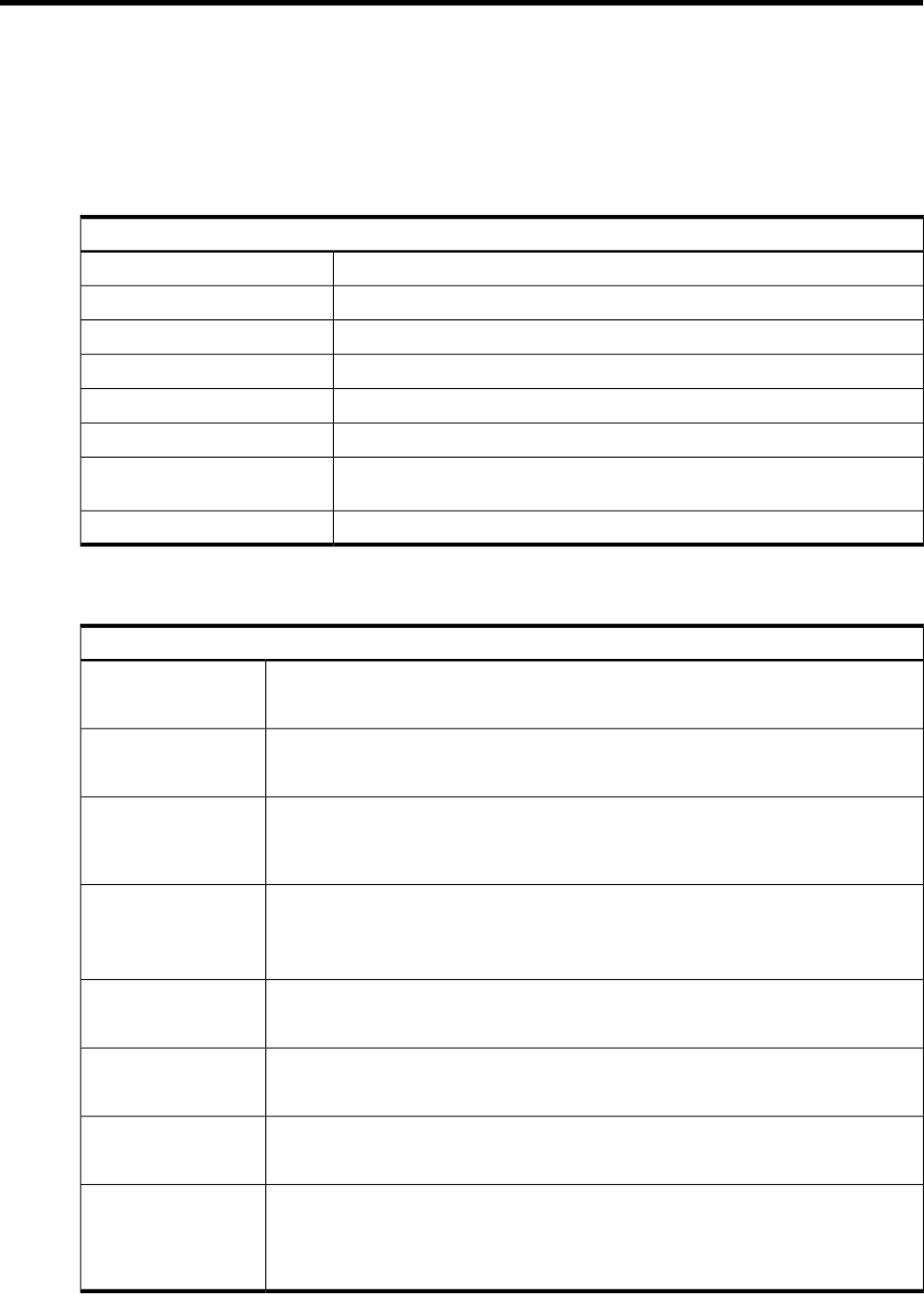
A Configuration Worksheet
Use this worksheet to plan your LDAP-UX Client Services configuration. For installation and
configuration details, refer to “Installing LDAP-UX Client Services” (page 23) for details.
Each of the following should be configured once for each domain, except "Proxy user DN," which
only needs to be configured once regardless of the number of domains in the system.
Table A-1 LDAP-UX Client Services Configuration Worksheet
LDAP-UX Client Services Configuration Worksheet
Directory administrator DN:
Directory server host:
Directory server port:
Configuration profile DN:
Base DN of user data:
Proxy user DN:
Source of user, group data, and
other name services:
Migration method:
Refer to the next page for an explanation and sample table.
Table A-2 LDAP-UX Client Services Configuration Worksheet Explanation
LDAP-UX Client Services Configuration Worksheet
The DN of a directory administrator allowed to modify the directory.
Example: CN=directory manager,DC=cup,DC=hp,DC=com
Directory administrator
DN:
The host name or IP address where your directory server is running.
Example: sys001.hp.com (12.34.56.78)
Directory server host:
The TCP port number your directory server is using. If you use SSL, the default port
number is 636. If you do not use SSL, the default port number is 389.
Example: 389
Directory server port:
The DN where your configuration profile is.
Example:
CN=profile1,CN=Configuration,DC=cup,DC=hp,DC=com
Configuration profile
DN:
The DN where your user and group data is.
Example: CN=Users,DC=cup,DC=hp,DC=com
Base DN of user data:
The DN of the proxy user, if needed.
Example: CN=Proxy User,CN=Users,DC=cup,DC=hp,DC=com
Proxy user DN:
Where you get your user and group data from to migrate into the directory.
Example: /etc/passwd and /etc/group on sys001
Source of user, group
data:
How you will migrate your user and group data into the directory, for example, using the
migration scripts.
Example: migrate_all_online_ads.sh edited to remove all but
migrate_passwd_ads.pl, migrate_group_ads.pl, and migrate_base.pl
Migration method:
157










