HP-UX IPSec Version A.03.02.02 Administrator's Guide HP-UX 11i version 2 and HP-UX 11i version 3 (762800-001, April 2014)
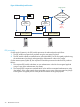
Figure 1 Shared key encryption
Data
Encryption
Algorithm
Encrypted Data
System A System B
Key
Data
Decryption
Algorithm
Encrypted Data
Key
Shared key cryptography alone does not provide protection against tampering. An intruder can
still intercept encrypted data and alter it before sending it to the correct destination. For this reason,
ESP also authenticates the encrypted data.
Shared key cryptography is also referred to as symmetric key cryptography (because the keys used
by both parties must be the same) and private key cryptography (because the two parties must
keep the key private).
Shared key hash functions
Shared key hash functions (also known as a symmetric key hash functions) are hash functions that
take a large block of variable-length data and a shared key as input and produce a small,
fixed-length hash value, or authentication code. The IPsec protocol suite uses a specific method for
producing the hash value and refers to the authentication value as the Hashed Message
Authentication Code (HMAC ).
Shared keyed hash functions are usually based on one-way hash functions: Starting with a hash
output value, it is difficult to create an input value that would generate the same output value, even
if no key is used. This makes it difficult for a third party to intercept a message and replace it with
a new message that generates the same authentication code. This ensures that only a holder of
the secret key can generate the correct authentication code.
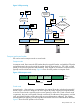
In Figure 2, the sender, System A, uses the plaintext (data) and the shared key to calculate an
HMAC for the data and sends the HMAC with the data. The recipient, System B, computes its own
HMAC value using the same shared secret key and data. The recipient then compares the result
with the transmitted HMAC. If the HMAC values match, the recipient is assured that the sender
knows the same secret key, confirming the identity of the sender. The recipient is also assured that
the data was not altered during transit.
IPsec protocol suite 33