HP-UX IPFilter A.03.05.13 Administrator's Guide: HP-UX 11i v3
Table Of Contents
- HP-UX IPFilter Version A.03.05.13 Administrator's Guide
- Legal Notices
- Table of Contents
- Preface: About This Document
- 1 Installing and Configuring HP-UX IPFilter
- Overview of HP-UX IPFilter Installation
- Step 1: Checking HP-UX IPFilter Installation Prerequisites
- Step 2: Loading HP-UX IPFilter Software
- Step 3: Determining the Rules for IPFilter
- Step 4: Adding Rules to the Rules Files
- Step 5: Loading IPFilter and NAT Rules
- Step 6: Verifying the Installation and Configuration
- Kernel Tunable Parameters
- Supported and Unsupported Interfaces
- Troubleshooting HP-UX IPFilter
- 2 HP-UX IPFilter on HP-UX 11i Version 3
- 3 Rules and Keywords
- IPFilter Configuration Files
- Basic Rules Processing
- IPFilter Keywords
- pass and block: Controlling IP Traffic
- in and out: Bidirectional Filtering
- quick: Optimizing IPFilter Rules Processing
- on: Filtering by Network Interfaces
- from and to: Filtering by IP Addresses and Subnets
- log: Tracking Packets on a System
- proto: Controlling Specific Protocols
- opt and ipopts: Filtering on IP Options
- icmp-type: Filtering ICMP Traffic by Type
- port: Filtering on TCP and UDP Ports
- keep state: Protecting TCP, UDP, and ICMP Sessions
- flags: Tight Filtering Based on TCP Header Flags
- keep frags: Letting Fragmented Packets Pass
- with frags: Dropping Fragmented Packets
- with short: Dropping Short Fragments
- return-rst: Responding to Blocked TCP Packets
- return-icmp: Responding to Blocked ICMP Packets
- dup-to: Drop-Safe Logging
- NAT Keywords
- 4 Dynamic Connection Allocation
- 5 Firewall Building Concepts
- Blocking Services by Port Number
- Using Keep State
- Using Keep State with UDP
- Using Keep State with ICMP
- Logging Techniques
- Improving Performance with Rule Groups
- Localhost Filtering
- Using the to
- Creating a Complete Filter by Interface
- Combining IP Address and Network Interface Filtering
- Using Bidirectional Filtering Capabilities
- Using port and proto to Create a Secure Filter
- 6 HP-UX IPFilter Utilities
- 7 HP-UX IPFilter and FTP
- 8 HP-UX IPFilter and RPC
- 9 HP-UX IPFilter and IPSec
- 10 HP-UX IPFilter and Serviceguard
- A HP-UX IPFilter Configuration Examples
- B HP-UX IPFilter Static Linking
- C Performance Guidelines
- Index
Rules and Keywords
IPFilter Keywords
Chapter 344
keep state: Protecting TCP, UDP, and ICMP Sessions
Use keep state to identify and authorize individual TCP, UDP, and
ICMP sessions that pass multiple packets back and forth. keep state
enables IPFilter to distinguish legitimate traffic from port scanners and
DoS attacks.
IPFilter maintains a state table. The state table is a list of open TCP,
UDP, and ICMP sessions. If a packet matches an entry in the state table,
it passes through the firewall without being checked against the ruleset.
This enhances the performance of the IPFilter system.
IPFilter checks both inbound and outbound packets against the state
table. If either an inbound or an outbound packet matches a session in
the state table, it is not checked against the ruleset.
You can use keep state to limit the number of rules you must configure.
Use keep state to pass or block the first packet in a TCP, UDP, or ICMP
session. When a packet matches a keep state rule, and entry is added
to the state table. You do not need to configure rules for all the other
types of traffic that might pass within a specific session.
For example, you can use the keep state keyword with IPFilter rules to
protect an SSH server.
block out quick on lan0 all
pass in quick on lan0 proto tcp from any to 20.20.20.1/32 port
= 22 keep state
Using the keep state keyword, after the first SYN packet is received by
the SSH server, an entry is made in the IPFilter state table. The
remainder of the SSH session continues without any further packets
within the session being checked against the IPFilter ruleset. Therefore,
the outbound traffic can flow freely within the session, despite the
block-out rule specified.
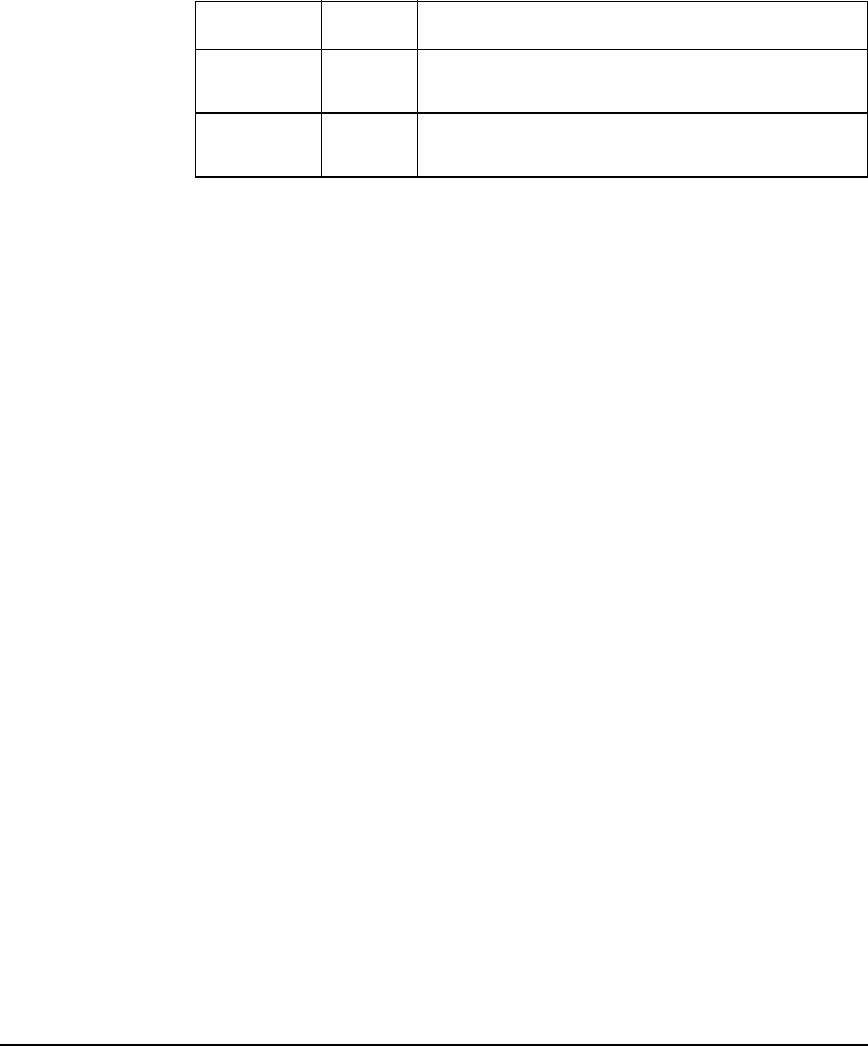
<= le true if port is less than or equal to configured
value
>= ge true if port is greater than or equal to
configured value
Operand Alias Result










