HP-UX Directory Server 8.1 console guide
• A list of acceptable compression methods
• A randomly-generated number
2. The server responds to the client:
• The chosen TLS/SSL version (this is the highest version in common with both the server
and client)
• The selected cipher suite (the most secure version the server and client have in common)
• The selected compression method (the most secure version the server and client have
in common)
• A randomly-generated number of its own
3. The server then sends its certificate. The server and client will use the public key in the
certificate to decrypt messages once the handshake ends and the secure session is established.
4. The client verifies the identity of the server using the information in the server certificate:
• The validity period (the expiration date of the server certificate)
• Whether the client possesses a copy of the CA certificate for the authority which issued
the server's certificate (whether the certificate was issued by a trusted CA)
• Verifying the digital signature of the issuing CA for the server certificate
• Whether the domain name for the server in the certificate subject name matches the
actual domain name of the server
5. Depending on the cipher suite being used, the client sends the server key material to use to
generate session keys to encrypt data. This key material can be public key or a master key
secret, which is used to derive the encryption keys.
6. Using the key material sent by the client, the randomly-generated numbers from the client
and server, and the selected cipher, the server and client independently derive the same
encryption keys.
7. The client sends a notification to the server that all subsequent messages from it will be
encrypted. It also sends a hash and a message authentication key, which are wrapped in the
client's encryption key.
8. The server successfully decrypts the client's message using its derived encryption keys.
9. The server then sends a hash and a MAC key to the client, wrapped in the server's encryption
key.
10. The client successfully decrypts the server's message using its derived encryption keys.
11. The TLS handshake closes, and the secure channel opens between the server and the client.
The Directory Console can be configured to be encrypted by SSL/TLS by configuring the Directory
Server to enable SSL in the Console.
6.2 Installing certificates
Before the Directory Server can be set to run in TLS/SSL, server and CA certificates must be
properly installed in the servers.
Obtaining and installing certificates consists of the following steps:
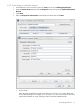
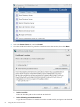
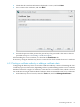
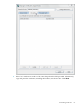
1. Generate a certificate request.
2. Send the certificate request to a certificate authority.
3. Install the server certificate.
4. Set the Directory Server to trust the certificate authority.
The Directory Server Console has two wizards to make it easier to request and install certificates.
62 Using SSL/TLS with the Console