HP-UX Directory Server 8.1 administrator guide
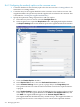
• Unless there is more than one instance of Directory Server configured, by default, there
are no consumers available in the drop-down menu.
• The port listed is the non-SSL port, even if the Directory Server instance is configured
to run over SSL. This port number is used only for identification of the Directory Server
instance in the Console; it does not specify the actual port number or protocol that is
used for replication.
• If SSL is enabled on the servers, it is possible to select the Using encrypted SSL
connection radio button for SSL client authentication. Otherwise, fill in the supplier
bind DN and password.
NOTE:
If attribute encryption is enabled, a secure connection must be used for the encrypted
attributes to be replicated.
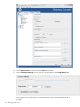
4. Select the connection type. There are three options:
• Use LDAP
This sets either a standard, unecrypted connection or allows SASL encryption, because
Directory Server supports SASL over standard LDAP but not SSL.
• Use TLS/SSL
This uses a secure connection over the server's secure LDAPS port, such as 636. This
setting is required to use TLS/SSL, but it cannot be set if the authentication will be
performed with SASL.
• Use Start TLS
This uses Start TLS to establish a secure connection over the server's standard port.
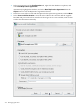
5. Select the appropriate authentication method and supply the required information. This
gives the information that the supplier uses to authenticate and bind to the consumer server
to send updates.
• Simple means that the server connects over the standard port with no encryption. The
only required information is the bind DN and password for the Replication Manager
(which must exist on the consumer server).
• Server TLS/SSL Certificate uses the supplier's SSL certificate to authenticate to the
consumer server. A certificate must be installed on the supplier for certificate-based
authentication, and the consumer server must have certificate mapping configured so
that it can map the subject DN in the supplier's certificate to its Replication Manager
entry.
Configuring SSL and certificate mapping is described in Chapter 12 “Managing SSL”.
• SASL/DIGEST-MD5 requires the standard port to connect to the server. Like simple
authentication, this requires only the bind DN and password to authenticate.
• SASL/GSSAPI also requires the standard LDAP connection because the Directory Server
does not support using GSS-API over TLS/SSL.
The supplier server must have a Kerberos keytab (as in “About the KDC server and
keytabs”), and the consumer server must have a SASL mapping to map the supplier's
principal to the real replication manager entry (as in “Configuring SASL identity
mapping from the console”).
6. Click Next.
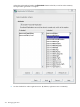
7. Fractional replication controls which entry attributes are replicated between servers. By
default, all attributes are replicated. To select attributes that will not be replicated to the
consumer, check the Enable Fractional Replication checkbox. Then, highlight the attribute
(or attributes) in the Included column on the right, and click Remove. All attributes that
8.6 Configuring cascading replication 359