HP CIFS Server Administrator Guide Version A.03.01.03 (5900-2006, October 2011)
Table Of Contents
- HP CIFS Server Administrator Guide Version A.03.01.03
- Contents
- About this document
- 1 Introduction to the HP CIFS Server
- 2 Installing and configuring HP CIFS Server
- HP CIFS Server requirements and limitations
- Step 1: Installing HP CIFS Server software
- Step 2: Running the configuration script
- Step 3: Modify the configuration
- Step 4: Starting HP CIFS Server
- Other Samba configuration issues
- 3 Managing HP-UX file access permissions from Windows NT/XP/2000/Vista/Windows 7
- Introduction
- UNIX file permissions and POSIX ACLs
- Using the Windows NT Explorer GUI to create ACLs
- Using the Windows Vista Explorer GUI to create ACLs
- POSIX ACLs and Windows 2000, Windows XP, Windows Vista, and Windows 7 clients
- HP CIFS Server Directory ACLs and Windows 2000, Windows XP, Windows Vista, and Windows 7 clients
- In conclusion
- 4 Windows style domains
- Introduction
- Configure HP CIFS Server as a PDC
- Configure HP CIFS Server as a BDC
- Domain member server
- Create the Machine Trust Accounts
- Configure domain users
- Join a Windows client to a Samba domain
- Roaming profiles
- Configuring user logon scripts
- Home drive mapping support
- Trust relationships
- 5 Windows 2003 and Windows 2008 domains
- 6 LDAP integration support
- Overview
- Network environments
- Summary of installing and configuring
- Installing and configuring your Directory Server
- Installing LDAP-UX Client Services on an HP CIFS Server
- Configuring the LDAP-UX Client Services
- Enabling Secure Sockets Layer (SSL)
- Extending the Samba subschema into your Directory Server
- Migrating your data to the Directory Server
- Configuring the HP CIFS Server
- Creating Samba users in directory
- Management tools
- 7 Winbind support
- 8 Kerberos support
- 9 HP CIFS deployment models
- Introduction
- Samba Domain Model
- Windows Domain Model
- Unified Domain Model
- 10 Securing HP CIFS Server
- 11 Configuring HA HP CIFS
- 12 HP-UX configuration for HP CIFS
- 13 Tool reference
- Glossary
- Index
on your systems and enable HP CIFS Server with SSL. For detailed information on how to enable
SSL communication over LDAP, see “LDAP integration support” (page 78).
The HP CIFS Server accepts the highly secure Kerberos tickets for Windows 2000 Active Directory
configurations.
Protecting sensitive configuration files
The default permissions for HP CIFS Server configuration files have been carefully selected to ensure
security while providing appropriate accessibility. However, you need also to protect these
configuration files from unauthorized access. Be especially careful if you decide to locate them in
alternative directories.
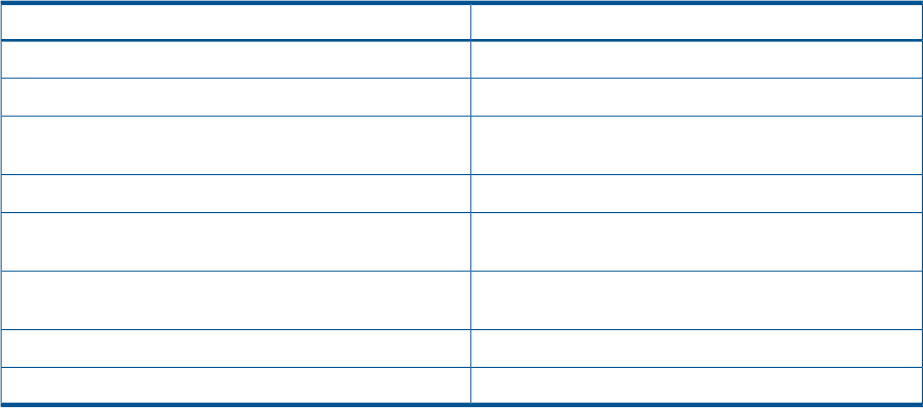
Table 6-1 describes a list of commonly used configuration files and their default locations. There
are also many smb.conf configuration parameters which permit alternate locations for these files
and many parameters that result in additional configuration files or scripts controlling run-time
actions not mentioned here.
Configuration file
Table 16 Configuration files
DescriptionFile
Master configuration file/etc/opt/samba/smb.conf
Log files/var/opt/samba/log.*
Database files containing important internal run-time
information
/var/opt/samba/locks/*.tdb
Data files containing system name and addresses/var/opt/samba/locks/*.dat
Master daemon process ID files used for starting, stopping,
and clustering scripts
/var/opt/samba/locks/*.pid
Database files contains important internal run-time
information
/var/opt/samba/private/*.tdb
Data file containing user name and password information/var/opt/samba/private/smbpasswd
Data file containing user name and password information/var/opt/samba/private/passdb.tdb
You need to be aware that the smbpasswd -w command stores the LDAP administrator's user
and password in the /var/opt/samba/private/secrets.tdb file in plain text.
Using %m Name Replacement macro with caution
The NetBIOS name of remote clients is substituted into the "%m" macro wherever it occurs in the
smb.conf configuration file. The use of contrived NetBIOS names may result in Samba using a
file path outside of the intended Samba directories. This can be used to cause Samba to append
data to important system files, which in turn can be used to compromise security on the server.
An immediate fix is to edit your smb.conf configuration file and remove all occurrences of the
macro "%m". Depending on the requirements of each site, other smb.confmacros may be suitable
replacements.
The log file option is the most vulnerable to this redefinition problem. The sample configuration
file contains the path,/var/opt/samba/log.%m. Using this default path does not create a
vulnerability unless there happens to exist a subdirectory in /var/opt/samba which starts with
the prefix "log.".
If you choose to maintain the use of the "%m" macro in thelog file option, you should use the
default value, /var/opt/samba/log.%m.
Security protection methods 135










