HP CIFS Server Administrator Guide Version A.03.01.03 (5900-2006, October 2011)
Table Of Contents
- HP CIFS Server Administrator Guide Version A.03.01.03
- Contents
- About this document
- 1 Introduction to the HP CIFS Server
- 2 Installing and configuring HP CIFS Server
- HP CIFS Server requirements and limitations
- Step 1: Installing HP CIFS Server software
- Step 2: Running the configuration script
- Step 3: Modify the configuration
- Step 4: Starting HP CIFS Server
- Other Samba configuration issues
- 3 Managing HP-UX file access permissions from Windows NT/XP/2000/Vista/Windows 7
- Introduction
- UNIX file permissions and POSIX ACLs
- Using the Windows NT Explorer GUI to create ACLs
- Using the Windows Vista Explorer GUI to create ACLs
- POSIX ACLs and Windows 2000, Windows XP, Windows Vista, and Windows 7 clients
- HP CIFS Server Directory ACLs and Windows 2000, Windows XP, Windows Vista, and Windows 7 clients
- In conclusion
- 4 Windows style domains
- Introduction
- Configure HP CIFS Server as a PDC
- Configure HP CIFS Server as a BDC
- Domain member server
- Create the Machine Trust Accounts
- Configure domain users
- Join a Windows client to a Samba domain
- Roaming profiles
- Configuring user logon scripts
- Home drive mapping support
- Trust relationships
- 5 Windows 2003 and Windows 2008 domains
- 6 LDAP integration support
- Overview
- Network environments
- Summary of installing and configuring
- Installing and configuring your Directory Server
- Installing LDAP-UX Client Services on an HP CIFS Server
- Configuring the LDAP-UX Client Services
- Enabling Secure Sockets Layer (SSL)
- Extending the Samba subschema into your Directory Server
- Migrating your data to the Directory Server
- Configuring the HP CIFS Server
- Creating Samba users in directory
- Management tools
- 7 Winbind support
- 8 Kerberos support
- 9 HP CIFS deployment models
- Introduction
- Samba Domain Model
- Windows Domain Model
- Unified Domain Model
- 10 Securing HP CIFS Server
- 11 Configuring HA HP CIFS
- 12 HP-UX configuration for HP CIFS
- 13 Tool reference
- Glossary
- Index
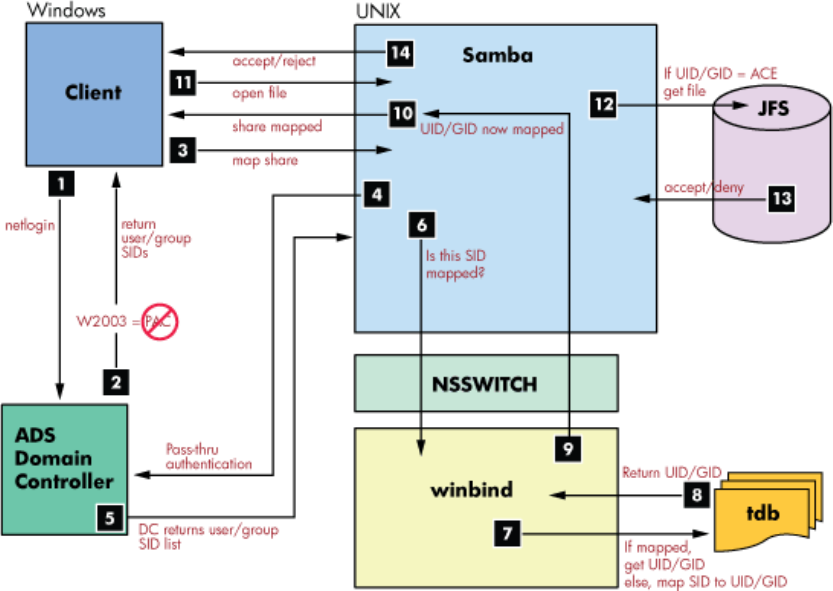
Figure 21 Winbind process flow
The following describes winbind process flow shown in Figure 7–1:
1. A Windows client logs in to the domain (authentication).
2. The Windows 2003 domain controller authenticates client and passes user security data.
3. The Windows client maps an HP CIFS share.
4. The HP CIFS Server passes the user name to Windows Domain Controller to verify the user is
a domain member.
5. The Windows Domain Controller returns the user authorization and member SID list.
6. The smbd daemon passes the SID and user information to the winbind daemon.
7. The Winbind daemon checks the SID and user name against ID mapping data in the Trivial
Database (TDB).Winbind either finds the existing mappings between the Windows SID and the
HP-UX UID/GID or creates a new map if no mapping currently exists.
8. Return mapped UID or GID from TDB database.
9. Winbind returns UID and GID mappings to smbd.
10. The HP CIFS Server presents the mapped share to the Windows client.
11. The Windows client opens file on the HP CIFS server share.
12. UID and GID are compared with file owner, group, and any ACE on ACL in the file system.
13. The File open action is accepted or denied based on the checking result in step 12.
14. The Samba sever displays the open status to the Windows client.
Winbind supports non-blocking, asynchronous functionality
For HP CIFS Server A.02.03 or later, winbind supports an almost completely non-blocking,
asynchronous request/reply implementation (with the exception of user and group enumeration).
With this new enhancement, winbind provides better scalability in large domain environments
and on high-latency networks.
100 Winbind support










